|
|

This chapter focuses on describing how you can configure basic system-wide, interface, and line capabilities. The following tasks are addressed:
Use the privileged EXEC command configure to begin configuration of the terminal server.
Begin by entering the privileged level of the EXEC. This is done by entering the enable command at the EXEC prompt:
TS>enable
The EXEC then prompts you for the privileged level password:
Password:
Type in the password. For security purposes, the password will not be displayed. (Also note that the password is case-sensitive.) When you enter the correct password, the system displays the privileged mode system prompt:
TS#
To begin configuration mode, enter the configure command at the privileged mode prompt:
TS#configure
When you enter this command, the EXEC prompts you for the source of the configuration subcommands.
Configuring from terminal, memory, or network [terminal]?
The default is to type in commands from the terminal console. Pressing the Return key begins this configuration method. Each configuration technique--terminal, memory, and network--is described in more detail later in this chapter.
The EXEC provides you with a simple editor for entering the configuration commands, and explains the editing functions:
Enter configuration commands, one per line. Edit with DELETE, CTRL/W, and CTRL/U;end with CTRL/Z
Table 1-1 lists the edit key functions and their meanings.
Key Meaning
Delete or Backspace Erases one character.
Ctrl-W Erases a word.
Ctrl-U Erases a line.
Ctrl-R Redisplays a line.
Return Executes single-line commands.
Ctrl-Z Ends configuration mode and returns to the EXEC.
Each configuration technique (terminal, memory, and network) is described in more detail later in this section.
The configuration subcommands are categorized by these functions:
The descriptions of the commands include the command type and give examples of their use.
As with EXEC commands, you can type configuration subcommands in uppercase letters, lowercase letters, or both. You may also shorten all commands and other keywords to unique abbreviations. You may add comments by preceding the line with an exclamation point (!). Comments do not affect command processing.
If you make a typing mistake, use the Delete or Backspace key to erase a character, Ctrl-W to erase a word, and Ctrl-U to erase a line. To redisplay a line, use Ctrl-R. See Table 1-1 for a list of valid commands.
The network server executes single-line commands when you press the Return key. The network server does not display confirmation messages as it executes the commands. If the network server encounters a problem, it displays an error message on the console terminal. When you type Ctrl-Z, the network server exits the configuration mode.
In most cases, you can negate a configuration subcommand or restore a default by typing no before the subcommand keyword. You can usually omit the arguments of the subcommand when you negate it with no. The command descriptions note any exceptions to these rules.
Following are some examples of configuration files to illustrate how to enter the configuration commands.
Use global configuration commands to enable functions that affect the entire system rather than a particular line or interface, and can appear any place within the configuration file. An example of this is the global configuration command to define the host name, or the name of the terminal server:
hostname termserv-1
Interface subcommands modify the operation of an interface such as an Ethernet, FDDI, or serial port. Interface subcommands always follow an interface command which defines the interface type.
The following example illustrates how to enable LAT and DEC MOP on interface Ethernet 0:
interface ethernet 0 mop enabled lat enabled
If you forget to enter the interface command, the system displays the message "must specify a network interface."
Line subcommands modify the operation of a serial terminal line. Line subcommands always follow a line command which defines the line number. If you forget to enter the line command, the system displays the message "must specify a line or range of lines."
The following example illustrates how to set the password on line 5:
line 5 password secretword
Type Ctrl-Z to end your configuration sessions, and the disable command to leave privileged level mode.
The EXEC allows you to enter the configuration subcommands from the console terminal, read the subcommands in from non-volatile memory, or read them in from a file on a remote host. The EXEC offers three commands that place the configuration information in these places for you.
Use the EXEC command write terminal to display current configuration information on your terminal screen.
Use the EXEC command write memory to copy current configuration information to non-volatile memory. This command stores all non-default configuration information as configuration commands in text format. This command also records a checksum for the information to protect against data corruption.
Use the EXEC commands write network to copy the current configuration information to a server host on the network.
Use the EXEC command show configuration to display information stored in non-volatile memory. You can also use this command and the write terminal command to find differences between the current configuration and that stored in non-volatile memory.
Use the EXEC command write erase to clear the contents of non-volatile memory.
Once you have specified an interface address and written information to non-volatile memory, the software, by default, looks for configuration information on a network host. Procedures later in this section explain how to set up configuration files on a remote host, and how to prevent this process, if you prefer not to store configuration information this way.
To specify configuration commands and subcommands from the console terminal, enter the EXEC command:
configureThe terminal server responds with a prompt asking you to specify the terminal, a file, or non-volatile memory as the source of configuration subcommands. To begin configuration, press Return or type terminal at the prompt displayed by the configure command to start command collection.
During command execution, the terminal server accepts one configuration subcommand per line. You can enter as many configuration subcommands as you want. Type Ctrl-Z when you finish entering configuration subcommands.
After making changes, write the configuration information into non-volatile memory or to a configuration file stored on a remote host. This will make checking, adding information to, and booting the configuration file an easier task. The procedures for writing information to non-volatile memory are described next.
After you enter the desired configuration information at the console terminal, use the privileged EXEC command:
write memoryThis EXEC command makes a copy of the configuration information in the non-volatile memory. The memory stores the current configuration information in text format as configuration commands, recording only nondefault settings. The memory is checksummed to guard against corrupted data.
As part of its startup sequence, the terminal server startup software always checks for configuration information in the non-volatile memory. Once the non-volatile memory holds valid configuration commands, the terminal server executes the commands automatically at startup. If the terminal server detects a problem with the non-volatile memory or the configuration information it contains, the terminal server may enter the setup mode, prompting for configuration information. Problems can include a bad checksum for the information in the non-volatile memory and the absence of critical information.
Even if the non-volatile memory provides configuration information, the terminal server can be made to attempt to load additional configuration information from the network server. You may want to keep an up-to-date version of configuration information on another host, where you can change it as necessary, and use the non-volatile memory as a bootstrap or backup mechanism. Instruct the terminal server to make this attempt by placing the following command in the non-volatile memory:
service configThe default is an implied no service config. This command limits the source of automatic configuration information to the non-volatile memory.
To display the configuration information stored in the non-volatile memory, use the privileged EXEC command:
show configurationTo clear the contents of the non-volatile memory, use the privileged EXEC command:
write eraseTo re-execute the configuration commands stored in non-volatile memory, enter this command at the configure mode prompt:
configure memoryUsing the configure memory command is like performing a soft reset of the system.
To store configuration information on a remote host, use the privileged EXEC command:
write networkThe command will prompt you for the destination host's IP address and a file name.
To retrieve and/or add to the configuration information stored on a host file, enter this command at the configure mode prompt:
networkThe terminal server may be configured to automatically load additional configuration information from a network host. You may want to keep an up-to-date version of configuration information on another host, where you can change it as necessary, and use the non-volatile memory as a bootstrap or backup mechanism. You can instruct the terminal server to load configuration information over the network by entering the service config subcommand and then writing the information to non-volatile memory using the write memory command.
After loading configuration information from the non-volatile memory, the terminal server will attempt to load two configuration files from remote hosts. The first is the network configuration file, which contains commands that apply to all terminal servers on a network. The second is the host configuration file, which contains commands that apply to one terminal server in particular.
The default name of the network configuration file is "network-confg." The default name for the host configuration file is taken from the host name. The host name can be specified by the hostname configuration subcommand or can be derived from the Domain Name System (DNS). Refer to the section on "Setting the Host Name" further ahead in this section for more information. To form the host configuration file name, the terminal server converts the host name to lower case, stripped of any DNS information, and appends "-confg." If no host name information is available, the default host configuration file name is "ts-confg." Other names for these configuration files can be set using the boot command, which is described in the "Setting Configuration File Specifications" section further ahead in this chapter.
The terminal server uses TFTP to load and save configuration files. By default, the terminal server uses the Internet address consisting of all ones (255.255.255.255) to broadcast TFTP Read Request messages. However, many hosts use an old style of broadcast address consisting of all zeros. You can change operation to accommodate hosts using the old style of broadcast address (0.0.0.0) with the ip broadcast-address interface subcommand.
If the terminal server fails to load a configuration file during startup, it tries again every ten minutes (default setting) until a host provides the requested files. With each failed attempt, the terminal server displays a message on the console terminal.
If the terminal server is unable to load the file named "network-confg," it displays the following message:
Booting network-confg ... [timed out]
To end these file load attempts, enter the following configuration command on the console terminal and save it in the non-volatile memory:
no service configThis command prevents the terminal server from trying to access nonexistent TFTP servers when it is booted.
Automatic configuration via network servers requires the terminal server first to determine its interface address from network servers, then to load configuration files.
The terminal server must identify the Internet address of its interface before it can complete its startup sequence. The terminal server first tries to find the required address in the non-volatile memory. If the attempt succeeds, the terminal server continues with the next step in the startup sequence, loading operating software or configuration information. If the attempt fails, the terminal server tries to get address information from other network servers.
To get address information from other network servers, the terminal server sends a broadcast request to all network servers. If a network server responds and supplies the required address information, the terminal server proceeds to load operating software or configuration information. If no network server responds, the terminal server displays an address request prompt on the console terminal and continues periodic network queries. The terminal server waits indefinitely for input from the console terminal or for a response from the network.
The terminal server uses different techniques for determining the address, depending on the type of network interface. For an Ethernet interface, the terminal server uses Reverse Address Resolution Protocol (RARP) and, if RARP fails, Boot Protocol (BootP). Both protocols send a broadcast message to all available network servers. The message requests the 32-bit Internet address corresponding to the 48-bit hardware address of the Ethernet interface.
Many UNIX systems support RARP and BootP, which are defined in RFC 903 and RFC 951, respectively.
After loading configuration information from the non-volatile memory (if any), the terminal server attempts to load two configuration files from other network servers. The network configuration file contains commands that apply to all Cisco Systems terminal servers and gateway servers on a network host. The host configuration file contains commands that apply to one terminal server in particular. If non-volatile memory is included with the system, it must include the service config command in order to cause the system to read configuration files from the network.
The first file the terminal server tries to load is the network configuration file "network-confg." Typically, the network configuration file contains commands to specify a default network, a default domain name, a list of name servers, and a set of host-name-to-address bindings. You can specify a new network configuration file name by putting the boot network command into the non-volatile memory.
After loading the network configuration file, the terminal server establishes its name. The terminal server first looks for name-to-address information provided by an ip host command in the network configuration file. If this attempt fails, the terminal server broadcasts a Domain Name System-based address-to-name query. If the terminal server receives no response, it uses "ts" as its host name.
By default, the terminal server uses its name to form a host configuration file name. To form this file name, the terminal server converts its name to all lowercase letters, removes all domain information, and appends "-confg."
Suppose the terminal server has the name chaff and the Internet address 192.31.7.18. The "network-confg" file would include this line:
ip host chaff 192.31.7.18
After loading the "network-confg" file, the terminal server would try to load the configuration file "chaff-confg" using TFTP. This configuration file would contain commands specific to chaff, such as interface and line configuration commands.
The terminal server uses TFTP to load configuration files. By default, the terminal server uses an Internet address of all ones to broadcast TFTP Read Request messages. However, many hosts use an old style of broadcast address consisting of all zeros. You can change terminal server operation to accommodate hosts using the old style of broadcast address using the ip broadcast-address interface subcommand.
If the terminal server fails to load a configuration file during startup, it tries again every 10 minutes until a host provides the requested files. With each (failed) attempt, the terminal server displays a message on the console terminal.
If the terminal server is unable to load the file named "network-confg," it displays the message:
Booting network-confg ... [timed out]
To end these file load attempts, enter the no service config command on the console terminal.
This section contains procedures and command descriptions for configuring the following system components and functions:
The hostname global configuration command specifies the host name for the network server, which is used in prompts and default configuration file names. To specify or modify the host name for the network server, use this command:
hostname nameThe argument name is the new host name for the network server and is case-sensitive. The default host name is TS for all Cisco terminal servers.
This command changes the host name to sandbox:
hostname sandbox
A banner is the message that the EXEC command interpreter displays whenever a user starts any EXEC process or activates a line.
The general form of the banner command is:
banner {motd | exec | incoming} d text dThe arguments motd, exec and incoming are keywords that control when the banner message is displayed. The use of these keywords is discussed in descriptions that follow. The argument d specifies a delimiting character of your choice. The argument text specifies the message to be shown on the screen whenever an interface line is activated.
Follow the banner command with one or more blank spaces, type the delimiting character, and then one or more lines of text, terminating the message with the second occurrence of the delimiting character.
The following example uses the # as a delimiting character:
banner motd # Building power will be off from 7:00 AM until 9:00 AM this coming Tuesday. #
To specify a general-purpose message-of-the-day type banner, use the banner motd global configuration command. The command syntax is:
banner motd d text dThis message-of-the-day type banner is displayed whenever a line is activated or when an incoming Telnet connection is created. When a new banner motd command is added to the configuration, it overwrites the existing banner command (with no keyword specified). Similarly, if a banner command is added to the configuration, any existing banner motd command is similarly overwritten.
To be able to display a message when an EXEC process is created, use the banner exec global configuration command. The command syntax is:
banner exec d text dThis specifies a message to be displayed when an EXEC process is created (line activated, or incoming connection to VTY).
To display an incoming message to a particular terminal line, use the banner incoming global configuration command.
An "incoming" connection is one initiated from the network interface side of the terminal server.
The command syntax is:
banner incoming d text dThis specifies a message to be displayed on incoming connections to particular terminal lines, for example, lines used for "milking machine" applications. "Milking machine" applications are discussed in more detail in "Configuring Reverse Connections" later in this chapter.
The EXEC banner can be suppressed on certain lines using the no exec-banner line subcommand. This line should not display the EXEC or MOTD banners when an EXEC is created.
Consider a box used to access a modem pool for either dial-in or dial-out usage. We want to show a different message to the user depending on whether they are dialing in, or dialing out. Furthermore, we want a message to tell that the box is going to be reloaded with new software tonight. The following example shows how to use the banner global configuration command and the no exec-banner line subcommand to accomplish this setting.
! lines 1 through 15 are connected to modems. line 1 15 modem inout ! ! Both messages are inappropriate for the VTYs. line vty 0 4 no exec-banner ! banner exec / This is cisco Systems training group terminal server. Unauthorized access prohibited. / ! ! banner incoming / You are connected to a Hayes-compatible modem. Enter the appropriate AT commands. Remember to reset anything to change before disconnecting. / ! ! banner motd / The terminal server will go down at 6pm for a software upgrade /
In normal system operation, there are several pools of different sized buffers. These pools grow and shrink based upon demand. Some buffers are temporary and are created and destroyed as warranted. Other buffers are permanently allocated and cannot be destroyed. The buffers command allows a network administrator to adjust initial buffer pool settings, as well as the limits at which temporary buffers are created and destroyed. It is normally not necessary to adjust these parameters; do so only after consulting with Cisco support personnel. Improper settings could adversely impact system performance. The full syntax of this command follows:
[no] buffers {small|middle|big|large|huge} {permanent|max-free|min-free|initial} numberThe first argument to the command is the name of the buffer pool; the name denotes the size of buffers in the pool--small, big, huge, etc. The default number of the buffers in a pool is determined by the hardware configuration, and can be displayed with the EXEC show buffers command.
The second argument specifies the buffer management parameter to be changed, and can be one of the following arguments:
The no buffers command with appropriate keywords and arguments restores the default buffer values.
In the following example, the system will try to keep at least 50 small buffers free.
buffers small min-free 50
In this example the system will try to keep no more than 200 medium buffers free.
buffers medium max-free 200
With the following command, the system will try to create one large temporary extra buffer, just after a reload:
buffers large initial 1
In this example the system will try to create one permanent huge buffer:
buffers huge permanent 1
To display statistics about the buffer pool on the system, use the command show buffers. For more information, refer to the "Monitoring System Processes" section in the "Managing the System" chapter
To display a specific message when a connection fails with a specified host, use the busy-message configuration command as follows:
busy-message hostname d message dThe busy-message command defines a message that the terminal server displays whenever an attempt to connect to the specified host fails. This command applies only to Telnet connections.
The argument hostname is the name of the host. Follow hostname with one or more blank spaces and a delimiting character (d) you choose. Then, type one or more lines of text (message), terminating the message with the second occurrence of the delimiting character.
To send a specific string after a successful connection, use the following command:
login-string hostname d message [%secp] [%secw] [%b] dThe login-string command defines a string of characters that the terminal server sends to a host after a successful connection attempt. The argument hostname is the name of the host to receive the message. Follow hostname with one or more blank spaces and a delimiting character (d) you choose. Then, type one or more lines of text message, terminating the message with the second occurrence of the delimiting character. This command applies only to rlogin and Telnet sessions.
The %secp option sets a pause in seconds.
The %secw option prevents users from issuing commands or keystrokes during a pause.
The %b option sends a Break character.
To use a percent sign in the login string, precede it with another percent sign; that is, type the characters "%%".
The no login-string subcommand removes the login string. This command applies only to rlogin and Telnet sessions.
To insert pauses into the login string embed a percent sign (%) followed by the number of seconds to pause and the letter "p."
In the following example the value "%5p" causes a five-second pause:
login-string office #ATDT 555-1234 %5p hello #
To enable the EXEC command lock, use the lockable configuration command:
lockableThe lockable command allows a terminal to be temporarily "locked" by the EXEC command lock.
The no lockable command reinstates the default, which does not allow the terminal to be locked.
State machines, in general, allow control of processes based upon a set of inputs. The current state of the device determines what will happen next given an expected input. The state-machine commands configure the terminal server to search for and recognize a particular sequence of characters, then cycle through a set of states. The user defines these states using the state-machine command; up to eight states can be defined. (Think of each state as a step the terminal server takes based upon the assigned configuration commands, and the type of information received.)
The purpose of a state machine is to allow packet dispatch based upon a sequence of characters, instead of a character. The dispatch-character commands (described in "State Machine Specification" section later in this chapter) enable packets to be buffered, then transmitted upon receipt of a character. The state-machine commands allow packets to be buffered, then transmitted upon receipt of a sequence of characters. This allows for packet transmission by pressing a function key, which is typically defined as a sequence of characters ("Esc [ A", as an example).
The terminal server code supports user specified state machines for determining whether data from an asynchronous port should be sent to the network. This is an extension of the concept of dispatch-character, and allows (for example) the equivalent of multicharacter dispatch strings.
To specify the transition criteria for the state of a particular state machine, use the state-machine command as follows:
state-machine name state firstchar lastchar nextstate [transmit] [delay]The argument name is the user-specified name for the state machine (used in the dispatch-machine line subcommand). There can be any number of state machines specified by the user, but each line can only have a single state machine associated with it.
The argument state defines which state is being modified. There are a maximum of eight states per state machine. Lines are initialized to state 0, and return to state 0 after a packet is transmitted.
The arguments firstchar and lastchar specify a range of characters. If the state machine is in the indicated state, and the next character input is within this range, go to the specified next state. Full 8-bit character comparisons are done, so the maximum value is 255. Take care that the line is configured to strip parity bits (or not generate them) or duplicate the low characters in the upper half of the space.
The argument nextstate defines the state to enter if the character is in the specified range.
Specifying the transmit keyword causes the packet to be transmitted and the state machine to be reset to state 0. Characters that occur that have not been explicitly defined to have a particular action return the state machine to state 0.
The optional delay keyword specifies that the destination state is transitory. If no additional input is received, the packet will be sent after 100 mS, and the state reset to 0.
For more information on setting the state machine for TCP, see the section "State Machine Specification." The following two examples show two different ways to set up state machines:
This first example is on the same line as an asynchronously-based packet format. A packet is terminated by a sequence DLE, ETX, CHKSUM, (16, 3, some number) DLE can occur in the packet itself if escaped by another DLE. (In particular, this means that the sequence DLE, DLE, ETX, X should not terminate the packet.)
Use a long dispatch-timeout to ensure that large packets can be generated and to prevent the line from getting permanently stuck in the event of lost data.
!If we see the first DLE, go to state 1 (from state 0) ! state-machine packet 0 16 16 1 ! ! If we see ETX after the DLE, go to state 2, otherwise (including ! another DLE) return to state 0 ! state-machine packet 1 3 3 2 ! ! In state 2, receipt of the checksum causes the packet to be sent ! state-machine packet 2 0 255 transmit ! ! Add this state machine to the appropriate lines ! line 1 20 dispatch-machine packet
The second example attempts to ensure that the characters from the function keys on an ANSI terminal are all lumped together into a single packet. This ensures that systems that attempt to distinguish between function keys and the same bytes typed individually do not become confused by variable network delays. An ANSI function key usually generates "Esc [ random upper-case-alpha:"
! Recall that the default is to remain in state 0 without ! transmitting anything. We want normal type-in to be transmitted ! immediately ! state-machine function 0 0 255 transmit ! ! Except for "escape," which starts waiting for the rest of a ! function key. However, if the user types "escape" we want it ! to be transmitted pretty soon. This is what the "delay" ! keyword does. ! state-machine function 0 27 27 1 delay ! ! Again, "esc foo" should transmit immediately, unless foo is "[" ! state-machine function 1 0 255 transmit state-machine function 1 91 91 2 delay ! ! Finally, we want to collect perhaps many characters in state 2, ! Until we run into an upper case alphabetic character, or the ! line stays idle for a while. ! state-machine function 2 0 255 2 delay state-machine function 2 65 90 transmit
The Cisco terminal server derives the clock for 38400 bps from a programmable timer. The terminal server software lets the user re-program the timer to provide other baud rates that would otherwise be unavailable. The current software provides the ability to change this rate on a per-system basis only. To define extra baud rate for the box, use the extra-baudrate configuration command:
extra-baudrate numberThe argument number defines the extra baudrate available for the box. The possible values are: 57600, 38400, 28800, 23040, 16457, 14400, 12800, and 11520. The value specified in an extra-baudrate command replaces the value of 38400 as a possible argument in the terminal speed EXEC command, described in the section "Changing the Terminal Baud Rate" in the "Managing the System" chapter.
After using this command, the individual lines can have their speed changed using the normal baud rate configuration commands (tsxpeed, rxspeed, speed).
This section describes the global configuration commands used to configure both the network and the host configuration files.
To configure the system and file specifications, you need to be in the configuration command mode. To enter this mode, use the EXEC configure command.
The boot command changes default file names and may specify a server host for netbooting configuration files, boot image files, and the size buffer to configure for netbooting a host or network configuration file.
The network configuration file contains commands that apply to all network servers and terminal servers on a network. The default name of this file is "network-config." Refer to the "Configuration Methods" section earlier in this chapter for more details. To change the name of the "network-config" file use the following command:
boot network filename [address]The keyword network changes the network configuration file from "network-confg."
The argument filename is the new name for the network configuration file.
The argument address is the new broadcast address. If you omit the argument address, the terminal server uses the default broadcast address of "255.255.255.255." If you use address, you can specify a specific network host or a subnet broadcast address.
The host configuration file contains commands that apply to one network server in particular. To change the host configuration file name, use the following command:
boot host filename [address]The keyword host changes the host configuration file name to a name you specify in the filename argument.
By default, the terminal server uses its name to form a host configuration file name. To form this name, the terminal server converts its name to all lowercase letters, removes all domain information, and appends "-confg." By default, the host file name is "ts-confg."
A terminal server can execute its system software stored in ROM, or it can be configured to load a newer version across the network. Network loading is only supported on systems with at least 4 Mbytes of memory (for example, CSC/3 or expanded IGS). The system uses the default file name cisconn-cpu, where "nn" is a value from the configuration register and "cpu" is the processor board in the system. You can override this with the boot system command.
boot system filename [address]The keyword system indicates this is a request to set the system image filename. In this case, the argument filename is the file name of the operating software to load, and the argument address is the address of the network host holding that file.
To use the non-volatile memory option to specify netbooting, place a boot system command in the non-volatile memory. This command is used to specify both the file name of the operating software to load, and the Internet address of the server host holding that file.
This command uses the non-volatile memory to specify the file name /usr/local/tftpdir/cisco.ts2 to load, and the Internet address 192.7.31.19 of the server host holding that file:
boot system /usr/local/tftpdir/cisco.ts2 192.7.31.19
To remove a file-name-and-address pair from the list, use the no form of the boot command syntax.
The boot system command overrides the processor configuration register setting unless the register specifies the use of default (ROM) operating software. Therefore, to permit netbooting, set the configuration register bits on the processor card to any pattern other than 0-0-0-0 or 0-0-0-1.
Normally, the terminal server uses a buffer the size of the system non-volatile memory to hold configuration commands read from the network. You can increase this size if you have a very complex configuration using the boot buffersize command. The command syntax is:
boot buffersize bytesThe argument bytes specifies the size of the buffer to be used. By default it is the size of the non-volatile memory, and there is no minimum or maximum size that may be specified.
The EXEC commands write terminal and write network use the information specified by the buffersize keyword when performing their functions; see the "Configuration Methods" section earlier in this chapter for more information about these EXEC commands.
You can configure multiple instances of the boot commands. When issued, each command is executed in order and so can be used to begin a systematic search or to build a specific list. For example, you can issue multiple boot commands to build an ordered list of configuration-file-name-and-host-address pairs. The terminal server scans this list until it successfully loads the appropriate network or host configuration file or system boot image. In this example, the terminal server looks first for fred-confg on 192.31.7.24 and, if it cannot load that file, then for wilma-confg on 192.31.7.19:
boot host /usr/local/tftpdir/fred-confg 192.31.7.24 boot host /usr/local/tftpdir/wilma-confg 192.31.7.19
If the terminal server cannot find either file, a background process tries at ten-minute intervals (default) to load one or the other of the files.
You may issue multiple instances of all variations of the boot command, including the no boot forms. This feature can be useful for removing configuration files. To remove a configuration file-name and host-address pair from the list, use the no form of the boot command syntax.
This section describes how to configure password protection and terminal access security.
You may set passwords to control access to the privileged command level and to individual lines. Additionally, you can configure a terminal server to use a special protocol called Terminal Access Controller Access Control System (TACACS) to allow a finer level of control using a server running on a timesharing system. The Defense Data Network (DDN) developed TACACS to control access to its TAC terminal servers; Cisco patterned its TACACS support after the DDN application.
Additional protection by use of access lists may also be required. The use of access lists applies to TCP/IP-based connections. Refer to the "Configuring TCP/IP" chapter for more information.
To assign a password for the privileged command level, use the enable password global configuration command:
enable password passwordThe argument password is case-sensitive and specifies the password prompted for in response to the EXEC command enable. The password argument may contain any alphanumeric characters, including spaces, up to 80 characters. The password checking is also case-sensitive. The password Secret is different than the password secret, for example, and the password two words is an acceptable password.
When you use the enable command at the console terminal, the EXEC will not prompt for a password if the privileged mode password is not set. This behavior allows access to the configure command to enter configuration command collection mode, so you can set parameters--such as the password for the privileged command level--for other lines. To restrict access to the console line, set a line password as described in the "Establishing Line Passwords" section later in this chapter.
This example sets the password secretword for the privileged command level on all lines, including the console:
enable password secretword
When an EXEC is started on a line with password protection, the EXEC prompts for the password. If the user enters the correct password, the EXEC prints its normal privileged prompt. The user may try three times to enter a password before the EXEC exits and returns the terminal to the idle state.
To specify a password, use the password line subcommand. The command syntax looks like this:
password textThe text argument may contain any alphanumeric characters, including spaces, up to 80 characters. The password checking is also case sensitive. The password Secret is different than the password secret, for example, and the password two words is an acceptable password.
To enable checking for the password specified by the password command, use the line subcommand login:
loginAlternatively, to cause the TACACS-style user ID and password checking mechanism to be used instead, use the following subcommand:
login tacacsTo disable all password checking, use the command:
no loginThe terminal server prints the message-of-the-day banner before prompting for a password, so the user immediately sees messages such as "no trespassing" notifications. By default, virtual terminals require a password. If you do not set a password for a virtual terminal, it will respond to attempted connections by displaying an error message and closing the connection. Use the no login subcommand to disable this behavior and allow connections without a password.
This example sets the password letmein on line 5:
line 5 password letmein login
If your terminal server has a non-volatile memory option, you can "lock yourself out" if you enable password checking on the console terminal line and then forget the line password. To recover from this situation, force the network server into factory diagnostic mode by turning off the terminal server, insert a jumper in bit 15 of the processor configuration register and turn on the network server. The processor configuration registers are described in Appendix A, "CPU Bootstrap Program," in the Modular Products Hardware Installation and Reference publication.
When the network server restarts in factory diagnostic mode, it does not read the non-volatile memory, thus avoiding the command to set a password for the console terminal. At the prompt, type show config to display the password in the configuration file. Do not change anything in the factory diagnostic mode. To resume normal operation, turn off the network server, remove the jumper from bit 15 (or bit 7) of the configuration register, and turn on the network server again. Log in to the network server with the password which was shown in the configuration file earlier. On the STS-10x, press the Break key while the system is first booting, and issue the "O/R" command at the ROM monitor. Next issue the "i" and "b" commands at the ROM monitor.
Cisco Systems provides unsupported versions of a standard and an extended TACACS server that run on most UNIX systems available from Cisco through the IP FTP protocol. The servers may be used to create UNIX accounting records to track use of server usage.
What follows are the configuration commands that tailor the behavior of the standard TACACS software running on the Cisco server.
The tacacs-server host global configuration command specifies a TACACS host. The command syntax is:
tacacs-server host nameThe argument name is the name or Internet address of the host. You can use multiple tacacs-server host subcommands to specify multiple hosts. The server will search for the hosts in the order you specify them.
The no tacacs-server host global configuration command deletes the specified name or address.
The tacacs-server attempts global configuration command controls the number of login attempts that may be made on a line set up for TACACS verification. The command syntax is:
tacacs-server attempts countThe argument count is the number of attempts. The default is three attempts.
The no tacacs-server attempts global configuration command restores the default.
This command changes the login attempt to just one try:
tacacs-server attempts 1
The tacacs-server retransmit global configuration command specifies the number of times the server will search the list of TACACS server hosts before giving up. The server will try all servers, allowing each one to time-out before increasing the retransmit count. The command syntax is:
tacacs-server retransmit retriesThe argument retries is the retransmit count. The default is two retries.
The no tacacs-server retransmit global configuration command restores the default.
This command specifies a retransmit counter value of 5 times:
tacacs-server retransmit 5
The tacacs-server timeout global configuration command sets the interval the server waits for a server host to reply. The command syntax is:
tacacs-server timeout secondsThe argument seconds specifies the number of seconds. The default interval is 5 seconds.
The no tacacs-server timeout global configuration command restores the default.
This command changes the interval timer to 10 seconds:
tacacs-server timeout 10
If, when running the TACACS server, the TACACS server does not respond, the default action is to deny the request. The tacacs-server last-resort global configuration command can be used to change that default. The command syntax is:
tacacs-server last-resort {password|succeed}The command causes the network server to request the privileged password as verification, or forces successful login without further input from the user, depending upon the keyword specified, as follows:
The no tacacs-server last-resort global configuration command restores the system to the default behavior.
The following variations of the enable command may be used to configure privileged level command access using the TACACS protocol.
The enable use-tacacs global configuration command is used for setting the TACACS protocol for determining whether a user can access the privileged command level. The command syntax is:
enable use-tacacsIf this command is used, the EXEC enable command will ask the user for both a new user name and password pair. This pair is then passed to the TACACS server for authentication. If you are using the Extended TACACS, it will also pass any already-existing UNIX user identification code to the server.
The enable last-resort global configuration command allows the user to specify what happens if the TACACS servers used by the enable command do not respond. The command syntax is:
enable last-resort {succeed|password}The default action is to fail. Use of the keyword changes the action, as follows:
The no enable last-resort global configuration command restores the default.
What follows are the configuration commands that tailor the behavior of the extended TACACS server.
The tacacs-server extended global configuration command enables an extended TACACS mode. The command syntax is:
[no] tacacs-server extendedThis mode provides information about the terminal requests for use in setting up UNIX auditing trails and accounting files for tracking use of protocol translators, terminal servers and routers. Information includes responses from terminal servers and routers and validation of user requests. An unsupported, extended TACACS server is available from Cisco Systems using FTP for UNIX users who want to create the auditing programs. Extended TACACS differs from "standard" TACACS in that standard TACACS provides only user name and password information.
The tacacs-server notify global configuration command causes a message to be transmitted to the TACACS server with retransmission being performed by a background process for up to five minutes. The terminal user, however, receives an immediate response allowing access to the feature specified. The command syntax is:
tacacs-server notify {connect|slip|enable|logout}The optional keywords are used to specify notification of the TACACS server whenever someone does one of the following things:
The tacacs-server authenticate command requires a response from the network or terminal server to indicate whether the user may perform the indicated action. The command syntax is:
tacacs-server authenticate {connect|slip|enable}Actions which require a response include the following, specified as optional keywords:
Networks that cannot support a TACACS service may still wish to use a user name-based authentication system. In addition, it may be useful to define "special" user names that get special treatment (for example, an "info" user name that does not require a password, but connects the user to a general purpose information service.)
The terminal server software supports these needs by implementing a local username configuration command. The format for the command is:
username name [nopassword | password encryptiontype password]Multiple username commands can be used to specify options for a single user.
The nopassword keyword means that no password is required for this user to log in. This is usually most useful in combination with the autocommand keyword.
The password keyword specifies a possibly encrypted password for this user name.
The encryptiontype argument is a single digit number. Currently defined encryption types are 0, which means no encryption, and 7, which specifies a Cisco-specified encryption algorithm. Passwords entered unencrypted are written out with the Cisco encryption. Ap assword can contain imbedded spaces and must be the last option specified in the username command.
The accesslist keyword specifies an outgoing access list that overrides the access list specified in the access class line configuration subcommand. It is used for the duration of the user's session. The access list number is specified by the number argument.
The autocommand keyword causes the command specified by the command argument to be issued automatically after the user logs in. When the command is complete, the session is terminated. As the command can be any length and contain imbedded spaces, commands using the autocommand keyword must be the last option on the line.
The nohangup keyword prevents the terminal server from disconnecting the user after an automatic command (set up with the autocommand keyword) has completed. Instead, the user gets another login prompt.
To implement a service similar to the UNIX who command, which can be given at the login prompt and lists the current users of the terminal server, the command takes the following form:
username who nopassword nohangup autocommand show users
To implement an information service that does not require a password to be used, the command might look like the following:
username info nopassword noescape autocommand telnet nic.ddn.mil
To implement an ID that will work even if the TACACS servers all break, the command is as follows:
username superuser password superpassword
Simple Network Management Protocol (SNMP) provides a way to access and set configuration and runtime parameters for the network server. Cisco System's implementation of SNMP is compatible with RFCs 1155, 1157, and 1213. The Cisco Management Information Base (MIB) supports all of RFCs 1155 and 1213, and provides Cisco-specific variables.
A separate document, available in RFC 1212-type format (concise MIB), describes all the Cisco-specific SNMP variables in the Cisco portion of the MIB. It also describe what is required to establish minimum configuration. Contact Cisco Systems to obtain a copy of this document, which includes instructions for accessing the variables using SNMP.
To set up an access list that determines which hosts can send requests to the network server, use the snmp-server access-list global configuration command. The command syntax is:
snmp-server access-list listThis command sends all traps to the host. The network server ignores packets from hosts that the access list denies.
The argument list is an integer from 1 through 99 that specifies an IP access list number. The access list applies only to the global read-only SNMP agent configured with the command snmp-server community.
The no snmp-server access-list global configuration command removes the specified access list.
This command sends traps to all hosts defined by access list 21:
snmp-server access-list 21
In this example, any host using the community string braves has SNMP read-only access to the router.
snmp-server access-list 1 snmp-server community bluejay rw snmp-server community braves ro ! access-list 1 permit 142.111.131.1 access-list 1 deny 0.0.0.0 255.255.255.255
This example configuration restricts SNMP read-only access to only the host at 142.111.131.1:
snmp-server community bluejay rw snmp-server community braves ro 1 ! access-list 1 permit 142.111.131.1 access-list 1 deny 0.0.0.0 255.255.255.255
In comparing the two examples, consider that the second example restricts read-only access to only the host at 142.111.131.1. The first example allows any host SNMP read-only access if it has the community string, and disallows SNMP read-only access to all hosts with the community string braves except the host 142.111.131.1.
To set up the community access string, use the snmp-server community global configuration command. The command syntax is:
snmp-server community [string [RO|RW] [list]]This command enables SNMP server operation on the network server. The argument string specifies a community string that acts like a password and permits access to the SNMP protocol.
By default, an SNMP community string permits read-only access (keyword RO); use the keyword RW to allow read-write access. The optional argument list is an integer from 1 through 99 that specifies an access list of Internet addresses that may use the community string.
The no snmp-server community global configuration command removes the specified community string or access list.
This command assigns the string comaccess to the SNMP and allows read-only and specifies that Internet address list 4 may use the community string:
snmp-server community comaccess RO 4
To establish the message queue length for each TRAP host, use the snmp-server queue-length global configuration command. The command syntax is:
snmp-server queue-length lengthThis command defines the length of the message queue for each TRAP host.
The argument length is the number of TRAP events that can be held before the queue must be emptied; the default is 10. Once a TRAP message is successfully transmitted, software will continue to empty the queue, but never faster than at a rate of four TRAP messages per second.
This command establishes a message queue that traps 4 events before it must be emptied:
snmp-server queue-length 4
To establish the maximum packet size, use the snmp-server packetsize global configuration command. The command syntax is:
snmp-server packetsize bytesThis command allows control over the largest SNMP packet size permitted when the SNMP server is receiving a request or generating a reply.
The argument bytes is a byte count from 484 through 8192. The default is 484.
This command establishes a packet filtering of a maximum size of 1024 bytes:
snmp-server packetsize 1024
To specify the recipients of trap messages, use the snmp-server host global configuration command. The full syntax follows.
snmp-server host address community-string [snmp] [tty]This command specifies which host or hosts should receive trap messages. You need to issue the snmp-server host command once for each host acting as a trap recipient.
The argument address is the name or Internet address of the host. The argument community-string is the password-like community string set with the snmp-server community command.
The optional keywords define which traps are sent, as follows:
If you do not specify any optional keywords, the sending of all trap types is enabled.
If you specify multiple snmp-server host commands for a given host or address, the community string used is the one on the last command line you entered, and the traps sent are a combination of all the optional keywords you specified.
The no snmp-server host command removes the specified host.
This command sends all SNMP traps to 131.108.2.160:
snmp-server host 131.108.2.160
To turn these trap messages off, use the no snmp-server host command:
no snmp-server host 131.108.2.160
The following example causes all the SNMP traps to be sent to the host specified by the name cisco.com. The community string is defined to be comaccess.
snmp-server host cisco.com comaccess snmp
Suppose the initial configuration is as follows:
snmp-server host 131.108.2.3 public snmp
You then enter the following configuration command:
snmp-server host 131.108.2.3 private
This results in the following configuration, which uses the community string you specified last and the trap type snmp:
snmp-server host 131.108.2.3 private snmp
Starting again with the initial configuration, suppose you enter the following command:
snmp-server host 131.108.2.3 notpublic tty
This results in the following configuration, which uses the community string you specified last and the trap types snmp and tty:
snmp-server host 131.108.2.3 notpublic snmp tty
To modify the initial configuration so that only tty traps are sent, enter the following commands:
no snmp-server host 131.108.2.3 snmp-server host 131.108.2.3 public tty
To establish the TRAP message authentication, use the snmp-server trap-authentication global configuration command. The command syntax is:
snmp-server trap-authenticationThis command enables the network server to send a TRAP message when it receives a packet with an incorrect community string.
The SNMP specification requires that a TRAP message be generated for each packet with an incorrect community string. However, because this action can result in a security breach, the network server by default does not return a TRAP message when it receives an incorrect community string.
To define how often to try resending TRAP messages on the retransmission queue, use this global configuration command. The command syntax is:
snmp-server trap-timeout secondsThe argument seconds sets the interval for resending the messages. The default is set to 30 seconds.
This command sets an interval of 20 seconds to try resending TRAP messages on the retransmission queue:
snmp-server trap-timeout 20
Using SNMP packets, a network management tool can send messages to users on directly connected terminals, virtual terminals, and the terminal server's console. This facility operates in a similar fashion to the EXEC send command; however, the SNMP request that causes the message to be issued to the users also specifies the action to be taken after the message is delivered. One possible action is a "shutdown" request.
Requesting "shutdown-after-message" is similar to issuing a send command followed by a reload command. Because the ability to cause a reload from the network is a powerful feature, it is protected by this configuration command. To use this SNMP message reload feature the device configuration must include the snmp-server system-shutdown global configuration command. The syntax of this command is as follows:
[no] snmp-server system-shutdownThe no snmp-server system-shutdown option prevents an SNMP system-shutdown request (from an SNMP manager) from resetting the Cisco agent.
To understand how to use this feature with SNMP requests, read the document "mib.txt" available by anonymous ftp from ftp.cisco.com. This document is available in RFC 1212-type format. It describes all the Cisco-specific SNMP variables in the Cisco portion of the MIB. It also describes what is required to establish minimum configuration. Contact Cisco Systems to obtain a copy of this document, which includes instructions for accessing the variables using SNMP.
To disable SNMP server operations on the terminal server after it has been started, use the no snmp-server global configuration command. The command syntax is:
no snmp-serverThe service command tailors use by the network server of network-based services. Some service commands also configure system defaults; refer to the decimal-tty command for an example.
The command syntax is as follows:
[no] service keywordThe argument keyword is one of the following:
Use the service nagle subcommand to enable use of the Nagle algorithm, which limits TCP transmissions by ensuring only one packet is outstanding per TCP connection. This subcommand is useful in some networks with slow links. See RFC 896 for more information about use of the Nagle algorithm.
The no service subcommand disables the specified service or function.
To disable TFTP autoloading of configuration files, enter this subcommand:
service config
To disable use of the Nagle algorithm, enter this subcommand:
no service nagle
The TCP keepalive capability allows a terminal server to detect when the host with which it is communicating experiences a system failure, even if data stops being transmitted (in either direction). This is most useful on incoming connections. For example, if a host failure occurs while talking to a printer, the terminal server may never notice, since the printer does not generate any traffic in the opposite direction. If keepalives are enabled, they are sent once every minute on otherwise idle connections. If five minutes pass and no keepalives are detected, the connection is closed. The connection will also be closed if the host replies to a keepalive packet with a reset packet. This will happen if the host crashes and comes back up again.
There are two global commands. They have the following syntax:
[no] service tcp-keepalives-inThe global configuration command service tcp-keepalives-in enables keepalives on incoming connections (connections initiated by a remote host). The global configuration command service tcp-keepalives-out enables keepalives on outgoing connections (connections initiated by a user of the terminal server).
The no service tcp-keepalives-in and no service tcp-keepalives-out commands disable support of the keepalives protocol. This is the default.
The show tcp command display includes keepalive statistics. The "wakeups" row shows how many keepalives have been transmitted without receiving any response (this is reset to 0 when a response is received).
By default, the terminal server sends the output from the EXEC command debug and system error messages to the console terminal.
To redirect these messages, as well as output from asynchronous events such as interface transition, to other destinations, use the logging configuration command with the appropriate destination options.
These destinations include the console terminal, virtual terminals, internal buffers, and UNIX hosts running a syslog server; the syslog format is compatible with 4.3 BSD UNIX.
The following sections describe how to implement these redirection options on the terminal server.
To configure the logging of messages, you need to be in the configuration command collection mode. To enter this mode use the EXEC command configure at the EXEC prompt. (Refer to the section on "Using the Configure Command" earlier in this chapter for more details on this process.)
Next you enable the message logging using the logging on command. The command syntax is:
logging onThis command enables message logging to all destinations except the console. This behavior is the default.
The no logging on command enables logging to the console terminal only.
The default logging device is the console; all messages are displayed on the console unless otherwise specified.
To log messages to an internal buffer, use the logging buffered command. The command syntax is:
logging bufferedThis command copies logging messages to an internal buffer instead of writing them to the console terminal.
The buffer is circular in nature, so newer messages overwrite older messages.
To display the messages that are logged in the buffer, use the EXEC command show logging. The first message displayed is the oldest message in the buffer.
The no logging buffered command cancels the use of the buffer and writes messages to the console terminal, which is the default.
To limit messages logged to the console based on severity, use the logging console command. The command syntax is:
logging console levelThis command limits the logging messages displayed on the console terminal to messages with a level at or below level.
The argument level is one of the following keywords, listed here in order from the most severe to the least severe level:
The default is to log messages to the console at the warnings level.
The no logging console command disables logging to the console terminal.
This example limits logging of messages to the console of level warnings or below:
logging console warnings
To limit messages logged to the terminal lines (monitors) based on severity, use the logging monitor command. The command syntax is:
logging monitor levelThis command limits the logging messages displayed on terminal lines other than the console line to messages with a level at or above level.
The argument level is one of the keywords described for the logging console command in the section on "Logging Messages to the Console."
To display logging messages on a terminal, use the privileged EXEC command terminal monitor.
The no logging monitor command disables logging to terminal lines other than the console line.
To log messages to syslog server host, use the logging command with the appropriate Internet address. The command syntax is:
[no] logging hostThe logging command identifies a syslog server host to receive logging messages.
The argument host is the name or the Internet address of the host.
By issuing this command more than once, you build a list of syslog servers that receive logging messages.
The no logging command deletes the syslog server with the specified address from the list of syslogs.
To limit messages logged to the syslog servers based on severity, use the logging trap command. The command syntax is:
logging trap levelThe logging trap command limits the logging messages sent to syslog servers to only the messages with a level at or above level.
The argument level is one of the keywords described for the logging console command in the "Logging Messages to the Console" section earlier in this chapter.
The no logging trap command disables logging to syslog servers.
Current software generates four categories of syslog messages:
The EXEC command show logging displays the addresses and levels associated with the current logging setup. The output of this command also includes ancillary statistics.
To set up the syslog daemon on a 4.3 BSD UNIX system, include a line such as the following in the file /etc/syslog.conf:
local7.debugging /usr/adm/logs/tiplog
The local7 keyword specifies the logging facility to be used.
The debugging argument specifies the syslog level. (Refer to the previous level arguments list for other arguments that can be listed.)
The UNIX system sends messages at or below this level to the file specified in the next field. The file must already exist, and the syslog daemon must have permission to write to it.
This section describes the commands for configuring terminals and their characteristics.
To configure your console and virtual terminal lines you need to be in the configuration command collection mode. To enter this mode use the EXEC command configure at the EXEC prompt. (Refer to the section on "Using the Configure Command" earlier in this chapter for detailed instructions.)
To start configuring a terminal line, use the line command. This command identifies a specific line for configuration and starts the line configuration command collection. The command syntax is:
line [type-keyword] first-line [last-line]This command can take up to three arguments: a keyword, a line number, or a range of lines numbers.
The optional argument type-keyword specifies the type of line to be configured, it is one of the following keywords:
When the line type is specified, the argument first-line is the relative number of the terminal line (or the first line in a contiguous group) you want to configure. Numbering begins with 0 (zero).
The optional argument last-line is the relative number of the last line in a contiguous group you want to configure.
If you omit type-keyword, then first-line and last-line are absolute rather than relative line numbers. To display absolute line numbers, use the EXEC command systat.
The terminal server displays an error message if you do not specify a line number.
The line command enables you to easily configure a large group of lines all at once. After you set the defaults for the group, you can use additional line commands and subcommands to set special characteristics, such as location, for individual terminal lines.
Once in line configuration command collection mode, you can enter the line subcommands described in the rest of this section. The line configuration command collection mode ends when you enter a command that is not a line subcommand, or when you type Ctrl-Z.
The following sample command starts configuration for the first five asynchronous terminal lines, 0 through 4:
line tty 0 4
The line command keyword aux enables use of an auxiliary RS-232 DTE port available on all processor cards. This port is not available on the STS-10x. The command has the following syntax:
line aux 0This port can be used to attach to an RS-232 port of a CSU/DSU or protocol analyzer. Remote monitoring of that port can be performed by connecting to the TCP port whose number is 2000 decimal plus the line number of the auxiliary port. For example, if the auxiliary port was line 1, obtained from the EXEC command show users all, then the TCP port would be 2001. A special cable must be ordered from Cisco Systems to use the auxiliary port on the terminal server. Refer to your respective Hardware Installation and Reference publication for more information about this cable.
When specifying the auxiliary port, address it as line 0, as in this sample:
line aux 0
The auxiliary ports assert DTR only when a Telnet connection is established. The console port does not use RTS/CTS handshaking for flow control.
To configure the auxiliary port to support an EXEC process use the exec line subcommand. To allow the port to be configured as an auxiliary port, configure it in the following manner:
line aux 0 exec
No modem control signals are supported on this line. If an auto-answer modem is configured on the line, you must dial in, log in, then hang up. The EXEC is still present and may be used by the next person that dials into the number. The DTR signal will be active whenever an EXEC is configured on the auxiliary port.
When an EXEC is started on a line with password protection, the EXEC prompts for the password. If the user enters the correct password, the EXEC prints its normal prompt. The user may try three times to enter a password before the EXEC exits and returns the terminal to the idle state.
To specify a password, use the password line subcommand. The command syntax is as follows:
password textThe text argument may contain any alphanumeric characters, including spaces, up to 80 characters. The password checking is also case-sensitive.
The password Secret is different than the password secret, for example, and the password two words is an acceptable password.
The no password line subcommand removes the password.
This example sets the virtual terminal line 4 password to "secret":
line vty 4 login password secret
The terminal server displays a message on a console or terminal when there is no active EXEC. This message, referred to as the vacant message, is different from the banner message displayed when an EXEC process is activated. To turn the vacant message banner on or off, use the vacant-message line configuration subcommands:
vacant-messageThe vacant-message subcommand enables the banner to be displayed on the screen of an idle terminal.
The vacant-message subcommand without any arguments causes the default message to be displayed.
If a banner is desired, follow the vacant-message subcommand with one or more blank spaces and a delimiting character (d) of your choice. Then type one or more lines of text (message), terminating the text with the second occurrence of the delimiting character.
The following example turns on the system banner and displays this message:
line 0
vacant-message #
Welcome to cisco Systems, Inc.
This is the console terminal of the terminal server Sludge.
#
The no vacant-message line configuration subcommand suppresses a banner message.
The terminal server allows you to define a custom error message to be displayed when an incoming connection is attempted and all rotary-group or other lines are in use. If you do not define a custom message, when all lines are in use the user will receive the system-generated default message. You can use this additional text to provide the user with further instructions.
The refuse-message command allows you to define this error message. The syntax of this command is as follows:
refuse-message d message dThe argument d is a delimiting character of your choice.
The argument message is the message you want to show on the terminal.
To type the message, start with a delimiting character, followed by one or more lines of text, and then terminate the text with the second occurrence of the delimiting character. You should not use the delimiting character within the text of the message.
If you define a custom error message using this command, the terminal server:
Use the no refuse-message option to disable this command.
In the following example, line 5 is configured with the refuse-message command, and the user is given information about what to try next.
line 5 refuse-message /The dial-out modem is currently in use. Please try again later, or use the slow speed modem available as hostname"dialout-slow." /
To set the terminal type, use the terminal-type command. The command syntax is:
terminal-type terminal-nameThe terminal-type subcommand records, in the argument terminal-name, the type of terminal connected to the line for use in Telnet terminal-type negotiation; the Telnet terminal-type negotiation uses terminal name to inform the remote host of the terminal type. Text is used by TN3270 for display management.
The no terminal-type subcommand removes any information about the type of terminal.
To set the location of the terminal, use the location command. The command syntax is:
location textThe location subcommand enters information about the terminal location and/or status.
The argument text is the desired description. The description appears in the output of the EXEC command systat.
The no location subcommand removes this information.
To set the line as in an insecure location, use the insecure line configuration command. The command syntax is:
insecureThe information presented is only used by the LAT software, which reports such connections as "dialup" to remote systems.
In the previous versions of Cisco software, any line which used modem control was reported as "dialup" through the LAT protocol; this allows more direct control.
To set the terminal screen length, use the length subcommand. The command syntax is:
length screen-lengthThe argument screen-length is the number of lines on the screen.
The network server uses this value to determine when to pause during multiple-screen output.
The default length is 24 lines. A value of 0 (zero) disables pausing between screens of output.
To set the terminal screen width, use the width subcommand. The command syntax is:
width columnsThis subcommand sets the number of character columns on a single line of the attached terminal.
The default is 80 columns. The rlogin protocol uses columns to set up terminal parameters on a remote UNIX host.
To define or reinstate the default escape character, use the escape-character subcommand. The command syntax is:
escape-character decimal-numberThe escape-character subcommand defines the escape character.
The argument decimal-number is either the ASCII decimal representation of the character or a control sequence (Ctrl-E, for example).
The default escape character is Ctrl-^.
The no escape-character subcommand sets the escape character to Break.
To set the activation character, use the activation-character subcommand. The command syntax is:
activation-character decimal-numberThe activation-character subcommand defines the character you type at a vacant terminal to begin a terminal session.
The argument decimal-number is the ASCII decimal representation of the activation character. The default activation character is Return (ASCII character 13).
The no activation-character subcommand causes any character to activate a terminal.
To define the disconnect character, use the disconnect-character command. The command syntax is:
disconnect-character decimal-numberThis subcommand defines the character you type to end a session with the terminal server.
The argument decimal-number is the ASCII decimal representation of the session-disconnect character.
The Break character is represented by 0 (zero); NUL cannot be represented. By default, the no session-disconnect character is set.
To use the session-disconnect character in normal communications, precede it with the escape character.
The no disconnect-character subcommand removes the disconnect character.
To set the hold character, use the hold-character command. The command syntax is:
hold-character decimal-numberThe hold-character subcommand defines the local hold character used to pause output to the terminal screen.
The argument decimal-number is either the ASCII decimal representation of the hold character or else a control sequence (for example, Ctrl-P). The Break character is represented by 0 (zero); NUL cannot be represented.
By default, no local hold character is defined.
To continue the output, type any character after the hold character. To use the hold character in normal communications, precede it with the escape character.
To set the terminal parity, use the parity subcommand. The command syntax is:
parity {none | even | odd | space | mark}The parity subcommand defines the generation of the parity bit.
By default, the terminal server does no parity checking.
To set the terminal baud rate (speed of the lines), use one of the following speed subcommands. The command syntax is:
speed baudThe speed subcommand sets both the transmit (to terminal) and receive (from terminal) speeds.
The txspeed subcommand sets the transmit speed only.
The rxspeed subcommand sets the receive speed only.
The argument baud is typically set to 300, 1200, 2400, 4800, 9600, 19200, or 38400, but can be any user-defined speed in the range of 75 to 57600.
The default speed is 9600 baud.
To set the data bits, use the databits command. The command syntax is:
databits {5 | 6 | 7 | 8}The databits subcommand sets the number of data bits per character. If parity is being generated, specify 7 data bits per character. If no parity generation is in effect, specify 8 data bits per character.
The default is 8 data bits per character.
To set the number of the stop bits, use the stopbits command. The command syntax is:
stopbits {1 | 1.5 | 2}The stopbits subcommand sets the number of stop bits transmitted per byte. By default, the terminal server sends 2 stop bits.
To set the line to autobaud, use the autobaud subcommand. The command syntax is:
autobaudThe autobaud subcommand specifies automatic baud-rate detection over a range from 300 to 19200 baud.
To start communications with the terminal server using autobaud detection, you type multiple Returns at your terminal. A 600, 1800, or 19200 baud line requires three Returns to detect the baud rate. A line at any other baud rate requires only two Returns. If you type extra Returns after the baud rate is detected, the EXEC simply displays another system prompt.
To set the flow control, use the flowcontrol subcommand. The command syntax is:
flowcontrol {none | software [in | out] | hardware}The flowcontrol subcommand sets the method of data flow control between the terminal or other serial device and the terminal server.
The keyword software sets software flow control.
An additional keyword specifies the direction: in causes the terminal server to listen to flow control from the attached device, and out causes the terminal server to send flow control information to the attached device. If you do not specify a direction, both are assumed.
For software flow control, the default stop and start characters are Ctrl-S and Ctrl-Q (XOFF and XON). You can change them with the stop-character and start-character subcommands described later in this section.
The keyword hardware sets hardware flow control. For information about hardware flow control, see the relevant Cisco Hardware Installation and Reference publication. Only limited modem control is possible on a line using hardware flow control. Refer to "Configuring the Modem Control Lines" later in this chapter.
By default, no flow control method is set for a line.
To set the flow control start character, use the start-character subcommand. The command syntax is:
start-character decimal-numberThe start-character subcommand defines the character that signals the start of data transmission when software flow control is in effect.
The argument decimal-number is the ASCII decimal representation of the start character.
The default start character is Ctrl-Q (ASCII character 17).
To set the flow control stop character, use the stop-character subcommand. The command syntax is:
stop-character decimal-numberThe stop-character subcommand defines the character that signals the end of data transmission when software flow control is in effect.
The argument decimal-number is the ASCII decimal representation of the stop character.
The default stop character is Ctrl-S (ASCII character 19).
To set the padding on characters, use the padding command. The command syntax is:
padding decimal-number countThis subcommand sets padding for a specified output character.
The argument decimal-number is the ASCII decimal representation of the character.
The argument count is the number of NUL bytes sent after that character.
This example of the padding subcommand causes a Return (ASCII character *-13) with 25 NUL bytes:
padding 13 25
The no padding subcommand removes padding for the specified output character.
To determine the protocols that you will allow on individual lines and to select preferred (or default) protocols for these lines, use the transport line configuration subcommands.
There are three transport commands: transport output, transport input, and transport preferred.
The transport output line subcommand has the following syntax:
transport output [telnet] [lat] [rlogin] [none]This line subcommand specifies which protocols may be used for output on a line.
The transport input line subcommand has the following syntax:
transport input [telnet] [lat] [none]This line subcommand controls which protocols may be used to connect to a port.
The transport preferred line subcommand has the following syntax:
transport preferred [telnet|lat|rlogin|none]This line configuration subcommand specifies the preferred protocol to use when a command does not specify one.
For terminal servers that support LAT, the default protocol is LAT. For those that do not support LAT, the default is Telnet.
The keyword telnet specifies the remote terminal protocol called Telnet. It allows a user at one site to establish a TCP connection to a login server at another site.
The keyword lat specifies the LAT protocol which is a Local Area Transport protocol used most often to connect terminal servers to DEC hosts.
The rlogin keyword specifies the rlogin protocol. The rlogin setting is a special case of Telnet. If an rlogin attempt to a particular host has failed, the failure will be tracked, and subsequent connection attempts will use Telnet instead.
The none keyword specifies no protocol. The system normally assumes that any unrecognized command is a hostname. If the preferred transport is set to none, the system no longer makes that assumption. No connection will be attempted if the command is not recognized.
The following example sets the terminal line 1 preferred protocol to rlogin:
! line tty 1 transport preferred rlogin !
Refer to "Selecting the Preferred Terminal Transport Protocol" in the "Managing the System" chapter for more examples illustrating transport protocol specification.
To establish an automatic connection to a host, use the autohost command. The command syntax is:
autohost connect-argumentsThe autohost subcommand causes a line to automatically establish a connection to a host when an EXEC is started.
The argument connect-argument is any text appropriate as an argument to the connect EXEC command, including the hostname and any switches.
The autohost command is typically used to force an automatic call to a particular host when a user connects to a designated line on the terminal server.
The following example forces an automatic connection to a host named "dustbin" (which could be an IP address). In addition, uucp specifies TCP socket 25, and /stream enables a raw TCP stream with no Telnet control sequences.
autohost dustbin uucp /stream
Refer to "Configuring the Modem Control Lines" later in this chapter for more information about how EXEC sessions are started.
To set the dispatch character for the packets, use the dispatch-character command. The command syntax is:
dispatch-character decimal-number1 [decimal-number2 . . . decimal-number]This line subcommand defines a character that causes the packet to be sent, even if the dispatch timer has not expired.
The argument decimal-number is the ASCII decimal representation of the character, such as Return (ASCII character 13) for line-at-a-time transmissions.
The subcommand can take multiple arguments, so you can define any number of characters as the dispatch character.
The no dispatch-character subcommand removes the definition of the specified dispatch character.
To set the dispatch timer, use the dispatch-timeout command. The command syntax is:
dispatch-timeout millisecondsThis subcommand sets the dispatch timer.
The argument milliseconds specifies the number of milliseconds the terminal server waits after putting the first character into a packet buffer before sending the packet. During this interval, more characters may be added to the packet, thus increasing the processing efficiency of the remote host.
The no dispatch-timeout subcommand removes the time-out definition.
The dispatch-character and dispatch-timeout subcommands together cause the terminal server to attempt to buffer characters into larger-sized packets for transmission to the remote host. The terminal server normally dispatches each character as it is typed.
To specify the state machine for TCP packet dispatch, use the dispatch-machine command. The command syntax is:
dispatch-machine nameThe name argument specifies the name of the state machine which determines when to send packets on the asynchronous line.
Any dispatch-characters specified using the dispatch-character command are ignored if a state machine is also specified.
When the dispatch-timeout command is specified, a packet being built will be sent when the timer expires, and the state will be reset to 0.
If a packet becomes full, it will be sent regardless of the current state. However, the state is not reset. The packet size is dependent on the amount of traffic on the asynchronous line, as well as the dispatch time out. There is always room for 60 data bytes, and if the dispatch-timeout is 100 ms or greater, a packet size of 536 (data bytes) is allocated.
For more information about the state machine, see discussion on "Setting Up State Machines for TCP" in an earlier section of this chapter.
To turn the EXEC on or off, use the exec subcommand. The command syntax is:
[no] execThis exec subcommand determines whether or not the terminal server will start an EXEC process on the line. A serial printer, for example, should not have an EXEC started.
By default, the terminal server starts EXECs on all lines.
Use the exec-banner subcommand to control whether banners are displayed or suppressed. The command syntax is:
[no] exec-bannerThis line subcommand determines whether or not the terminal server will display the EXEC banner or message-of-the-day (MOTD) banner when an EXEC is created.
By default, the messages defined with banner motd and banner exec are displayed on all lines. The no exec-banner subcommand is useful for temporarily suppressing these banner messages. Specify exec-banner to reinstate.
This example suppresses the banner on asynchronous terminal lines 0 through 4:
line tty 0 4 no exec-banner
The EXEC command interpreter waits for a specified interval of time until the user starts input. If no input is detected, the EXEC resumes the current connection, or if no connections exist, it returns the terminal to the idle state and disconnects the incoming session.
To set this interval use the exec-limit subcommand. The command syntax is:
exec-timeout minutes [seconds]The argument minutes is the number of minutes.
The optional argument seconds specifies additional time intervals in seconds. The default interval is 10 minutes; an interval of 0 (zero) specifies no time-outs.
The no exec-timeout subcommand removes the time-out definition. It is the same as entering exec-timeout 0.
This sample subcommand sets a time interval of 2 minutes, 30 seconds:
exec-timeout 2 30
This sample subcommand sets an interval of 10 seconds:
exec-timeout 0 10
To set the interval for closing the connection when there is no input or output traffic, use the session-timeout command. The command syntax is:
session-timeout minutes [output]This subcommand sets the interval that the terminal server waits for traffic before closing the connection to a remote computer and returning the terminal to an idle state.
The argument minutes specifies the time interval in minutes.
The optional keyword output specifies that when traffic is sent to an asynchronous line from the terminal server (within the specified interval), the connection is retained. If the keyword output is not specified, the session time-out interval is based solely on detected input from the user.
The default interval is 0 (zero), indicating the terminal server maintains the connection indefinitely.
The following subcommand sets an interval of 20 minutes, and specifies that the time-out is subject to traffic detected from the user (input only):
session-timeout 20
The following subcommand sets an interval of 10 minutes, subject to traffic on the line in either direction:
session-timeout 10 output
The no session-timeout subcommand removes the time-out definition.
To set the maximum number of sessions, use the session-limit command. The command syntax is:
session-limit session-numberThe argument session-number specifies the maximum number of sessions.
To save configurations between sessions, use the private subcommand. The command syntax is:
[no] privateThe private subcommand ensures that the configuration options the user can set, will remain in effect between terminal sessions.
This behavior is desirable for terminals in private offices.
By default, user-set configuration options are cleared with the EXEC command exit or when the interval set with the exec-timeout subcommand has passed.
To enable terminal notification about pending output from other connections, use the notify command. The command syntax is:
[no] notifyThe notify subcommand sets a line to inform a user who has multiple, concurrent Telnet connections when output is pending on a connection other than the current connection.
This subcommand performs the same function as the EXEC command terminal notify described in "Changing Terminal Parameters" in the chapter "Managing the System."
The no notify subcommand ends notification.
The following example shows how to enter configuration command collection mode and set a password on the console line:
Configuring from terminal, memory, or network [terminal]? Enter configuration commands, one per line. Edit with DELETE, CTRL/W, and CTRL/U; end with CTRL/Z; abort with CTRL/C line 0 password secret <Ctrl-Z>
The next example shows how to configure a controlled line with no terminal EXEC, with software flow control set in both directions (to and from an attached device), and with transmit and receive speeds set to 19200 baud. The dispatch-timeout subcommand causes the terminal server to wait 100 milliseconds after the first character is put into a packet before sending the packet.
line 12 no exec flowcontrol software speed 19200 dispatch-timeout 100 <Ctrl-Z>
The final example shows how to configure a printer line. The subcommands turn off the terminal EXEC, turn on software flow control, set the stop bits to 1, and set the line speed to the maximum (38400 baud) to handle the requirements of a laser printer.
line 13 location Laser Writer/pubs no exec flowcontrol software stopbits 1 speed 38400 <Ctrl-Z>
Cisco Systems terminal servers use six RS-232 signals for each port, an arrangement that allows eight connections to be handled by one 50-pin Telco, RJ-11, or RJ-45 connectors. By using the six signals creatively, the terminal server can support the most popular forms of modem control and/or hardware flow control as well as high-speed dial-up modems.
The RS-232 output signals are called TXDATA and DTR. The input signals are called RXDATA, CTS, and RING. The sixth signal is ground. Depending on the type of modem control, these names may or may not correspond to the standard RS-232 signals which have similar names.
You configure the different types of modem control using subcommands of the line configuration command.
This section describes the line subcommands for configuring modem control. State diagrams accompany some of the subcommand descriptions to illustrate how the modem control would work.
The diagrams show two processes: the "create daemon" process creates a tty daemon that handles the incoming network connection and the "create EXEC" process creates the process that interprets user commands. (Refer to Figures 1-1 to 1-3.)
In the diagrams, the current signal state and the signal the line is watching are listed inside each box. The state of the line (as displayed by the EXEC command show line) is listed next to the box. Events that change that state appear in italic along the event path, with actions the software takes described within the ovals.
See the "Starting Line Configuration" section earlier in this manual for information about entering the line configuration command and its subcommands. Because of the way the terminal server software scans modem lines, the system operates more efficiently if all lines configured for modem control are contiguous.
To configure a modem control line, use the modem subcommand. The command syntax is:
[no] modem keywordThe argument keyword is one of the modem control keywords described in the following sections. For example, to configure a line for modem callout control, use the no modem callout subcommand.
The no modem subcommand removes modem control from a line.
By default, a terminal line is configured for no modem control.
Figure 1-1 illustrates line behavior when no modem control is set. The DTR output is always high, and CTS and RING are completely ignored. The terminal server creates an EXEC when the user types the activation character. Incoming TCP connections occur instantly if the line is not in use and can be closed only by the remote host.
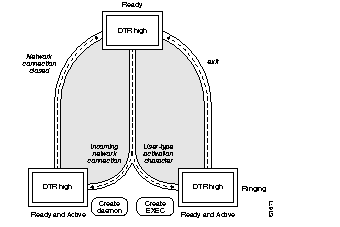
To configure a line for low DTR, use the modem dtr-active subcommand. The command syntax is:
modem dtr-activeThe modem dtr-active subcommand configures a line to leave DTR low unless the line has an active incoming connection or EXEC.
This behavior can be useful if the line is connected to an external device (for example, a timesharing system) that needs to know whether a line is in active use.
The modem dtr-active subcommand is similar to the no modem subcommand described earlier in this section.
To configure a line to require CTS, use the modem cts-required subcommand. The command syntax is:
modem cts-requiredThe modem cts-required subcommand supports lines that either the user or the network can activate.
This subcommand is useful for closing connections from a user's terminal when the terminal is turned off, and for preventing disabled printers and other devices in a rotary group from being considered. For more information about rotary groups, refer to the section on "Connections to One or More Lines (Rotary Group)" later in this chapter.
Figure 1-2 illustrates the modem cts-required process. This form of modem control requires that CTS be high throughout the use of the line. If CTS is not high, the user's typed input is ignored and incoming connections are refused (or step to the next line in a rotary group).
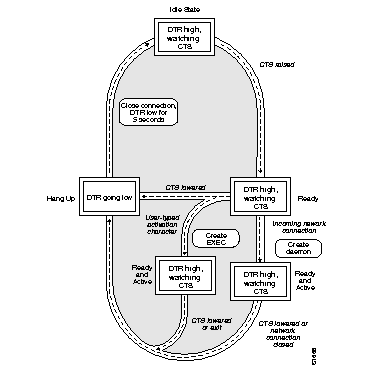
To configure a line for a high-speed modem, use the modem ri-is-cd subcommand. The command syntax is:
modem ri-is-cdThe modem ri-is-cd subcommand supports modems that can automatically handle telephone line activity, such as answering the telephone after a certain number of rings.
Configure the modem to answer the telephone on its own as long as DTR is high, drop connections when DTR is low, and use its CD signal to accurately reflect the presence of carrier. Wire the modem's CD signal (generally pin-8) to the terminal server's RING input (pin-22).
You can turn on the modem's hardware flow control independently to act on the status of the terminal server's CTS input. Wire CTS to whatever signal the modem uses for hardware flow control. If the modem expects to do hardware flow control in both directions, you may also need to wire the modem's flow control input to some other signal that the terminal server always has high (such as DTR).
Figure 1-3 illustrates the modem ri-is-cd process. When the terminal server detects a signal on the RING input of an idle line, it starts an EXEC or autobaud process on that line. If the RING signal disappears on an active line, the terminal server closes any open network connections and terminates the EXEC. If the user exits the EXEC or the terminal server terminates it because of no user input, the line hangs up the modem by lowering the DTR signal for five seconds. The modem is ready to accept another call after five seconds.
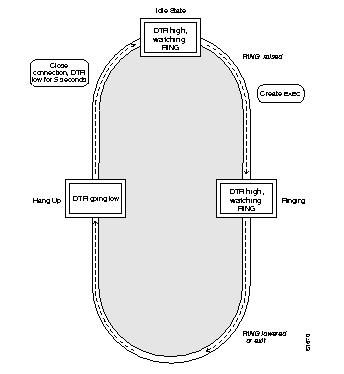
To configure a line for a dial-in modem, use the modem callin subcommand. The command syntax is:
modem callinThe modem callin subcommand supports dial-in modems that use DTR to control the off-hook status of the telephone line. Raising the DTR signal answers the telephone; lowering DTR hangs up the telephone.
Figure 1-4 illustrates the modem callin process. When a modem callin line is idle, it has DTR in a low state and waits for a transition to occur on the RING input. This transition causes the line to raise DTR and start watching the CTS signal from the modem. After the modem raises CTS, the terminal server creates an EXEC on the line. If the time-out interval (set with the modem answer-timeout subcommand) passes before the modem raises CTS, the line lowers DTR and returns to the idle state.
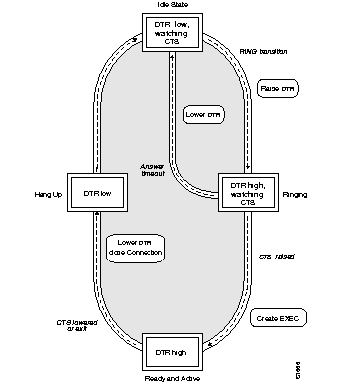
Although you can use the modem callin subcommand with newer modems, the modem ri-is-cd subcommand described earlier in this section is more appropriate. The modem ri-is-cd command frees up CTS for hardware flow control. Modern modems do not require the assertion of DTR to take a phone line off-hook.
To configure a line for reverse connections, use the modem callout subcommand. The command syntax is:
modem calloutThe modem callout subcommand supports ports connected to computers that expect to be connected to modems, an arrangement often called "milking machine" mode. (For more information, refer to the section on "Configuring Reverse Connections" later in this chapter). This subcommand causes the terminal server to behave somewhat like a modem.
Figure 1-5 illustrates the modem callout process. When the terminal server receives an incoming connection, it raises DTR and waits to see if the CTS become high as an indication that the host has noticed its signal. If the host does not respond within the interval set with the modem answer-timeout subcommand, the terminal server lowers DTR and drops the connection.
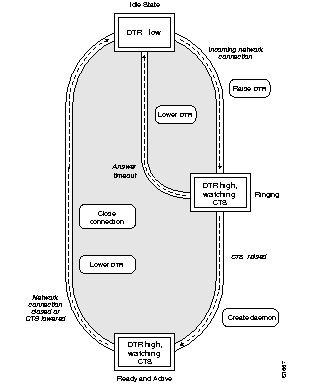
To configure a line for both incoming and outgoing calls, use the modem inout subcommand. The command syntax is:
modem inoutThe modem inout subcommand enables a line to be used for both incoming and outgoing calls on dial-in/dial-out modems. Note that the terminal server does not support any dialing protocols. Therefore, the host system software or the user must provide any special dialing commands when using the modem for outgoing calls.
Figure 1-6 illustrates the modem inout process. If the line is activated by raising RING, it behaves exactly as a line configured with the modem ri-is-cd subcommand, described earlier. If the line is activated by an incoming TCP connection, the line behaves similarly to a non-modem line.
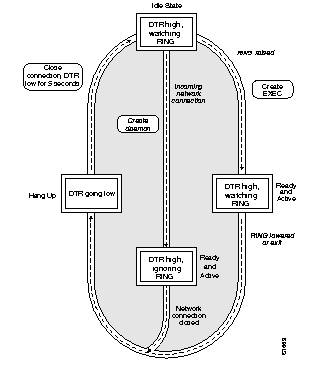
To configure line modem timing, use the modem answer-timeout subcommand. The command syntax is:
modem answer-timeout secondsThe modem answer-timeout subcommand sets the interval during which the terminal server raises DTR in response to RING and the modem responds to CTS. This behavior is useful for modems that take a long time to synchronize to the appropriate line speed.
The argument seconds specifies the interval in seconds.
The default is 15 seconds.
To configure automatic line disconnect, use the autohangup subcommand. The command syntax is:
autohangupThe autohangup subcommand causes the EXEC to issue the exit command when the last connection closes.
This subcommand is useful for UNIX UUCP applications that require this behavior, because UUCP scripts cannot issue the exit command to hang up the telephone.
Dial-up modems that operate over normal dial-up telephone lines at speeds of 9600 baud and higher are now available. These modems do not operate at a guaranteed throughput; instead, they operate at a speed dependent on the quality of the line, the effectiveness of data compression algorithms on the data being transmitted, and other variables. These modems use hardware flow control to stop the data from the host (by toggling some RS-232 signal) when they cannot take any more.
In addition to hardware flow control, dial-up modems require special software handling. For example, they must be configured to create an EXEC when a user dials in and to hang up when the user exits the EXEC. These modems must also be configured to close any existing network connections if the telephone line hangs up in the middle of a session.
Cisco Systems terminal servers support hardware flow control on their CTS input, which is also used by the normal modem handshake. To support both modem control and hardware flow control on the same line, use the modem ri-is-cd subcommand described earlier in this section.
The following commands may also be useful as you configure and use a high-speed modem:
In addition to initiating connections, the terminal server can receive incoming connections. This capability enables you to attach serial and parallel printers, modems, and other shared peripherals to the terminal server and drive them remotely from other systems.
The specific TCP port or socket to which you attach the device determines the type of service the terminal server provides on that line. When you attach the serial lines of a computer system or a data terminal switch to the serial lines of the terminal server, the terminal server acts as a network front-end for a host that does not support the TCP/IP protocols. This arrangement is sometimes called front-ending, reverse connection mode, or "milking machine" mode.
Connections to an individual line are most useful when a dial-out modem, parallel printer, or serial printer is attached to that terminal server line. To connect to an individual line, the remote host or terminal must specify a particular TCP port on the terminal server. If Telnet protocols are required, that port is 2000 (decimal) plus the decimal value of the line number.
If a raw TCP stream is required, the port is 4000 (decimal) plus the decimal line number. The raw TCP stream is usually the required mode for sending data to a printer.
The Telnet protocol requires that carriage return characters be translated into carriage returns and line-feed character pairs. You can turn this translation off by specifying the Telnet binary mode option. To specify this option, connect to port 6000 (decimal) plus the decimal line number.
As an example, assume that a laser printer is attached to line 10 of an MSM terminal server. Such a printer usually uses XON/XOFF software flow control. Because the terminal server will not receive an incoming connection if the line already has a process, you must ensure that an EXEC is not accidentally started. You must therefore configure it as follows:
line 10 flowcontrol software no exec
A host that wants to send data to the printer would connect to the terminal server on TCP port 4008, send the data, and then close the connection. (Remember that line number 10 octal equals 8 decimal.)
Connections may be made to the next free line in a group of lines, also called a rotary or hunt group. A line may be in only one rotary group; a rotary group may consist of a single line or many lines.
You define each group of lines with the rotary subcommand of the line configuration command. The command syntax is:
rotary groupThe rotary subcommand adds a line to the specified rotary group. The argument group is an integer between 1 and 100 that you choose to identify the rotary group. To list the defined rotary groups, use the privileged EXEC command show line. For more information, see the section "Monitoring System Processes" in the "Managing the System" chapter.
As for connections to an individual line, the remote host must specify a particular TCP port on the terminal server to connect to a rotary group. The available services are the same, but the TCP port numbers are different. Table 1-2 lists the services and port numbers for both rotary groups and individual lines.
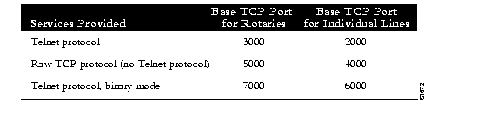
For example, if Telnet protocols are required, the remote host connects to the TCP port numbered 3000 (decimal) plus the rotary group number. If the rotary group identifier is 13, the corresponding TCP port is 3013.
If a raw TCP stream is required, the port is 5000 (decimal) plus the rotary group number. If rotary group 5 requires a raw TCP (printer) line, it connects to 5005.
If Telnet binary mode is required, the port is 7000 (decimal) plus the rotary group number.
Connections to a rotary group can also take advantage of these features:
This section describes the commands for configuring the system network interface.
The terminal server displays the name of its interface on the console terminal during startup. To display complete information about the interface, use the EXEC command show interfaces. For more information, see the "Monitoring System Processes" section in the "Managing the System" chapter.
In configuration command collection mode, start configuring an interface with the interface command. This command identifies a specific interface for configuration and starts interface configuration command collection. The command syntax is:
interface type unitThe argument type is one of the following generic names for the installed interface: ethernet, serial, or tokenring. The terminal server interface is usually type ethernet.
The argument unit is a positive integer that specifies the nth interface of type type, starting with 0 (zero) for the first interface of that type.
This command configures the interface of type ethernet with unit 0:
interface ethernet 0
This command configure the interface of type serial with unit 0:
interface serial 0
This command configure the interface of type tokenring with unit 0:
interface tokenring 0
In interface configuration command collection mode, you can enter the interface subcommands described in the rest of this section. The interface configuration command collection mode ends when you enter a command that is not an interface subcommand, or when you type Ctrl-Z.
The trerminal server displays the name of its interface on the console terminal during startup. To display complete information about the interface, use the show interfaces command. For more information, refer to the "Monitoring System Processes" section in the "Managing the System" chapter.
Configure the CSC-R16 token ring interface as follows:
This step is not necessary for the CSC-R token ring interface card.
Optionally, terminal servers on a Token Ring network in a source-route bridging environment must support the collection and use of RIF information, to provide necessary path information to the host. The following tasks are necessary to enable the RIF.
The following sections describe these tasks. For further information about the token ring interface and routing information fields, see the Router Products Configuration and Reference manual.
Set the speed of the token ring interface. Choices are 4 or 16 megabits per second. Use this command:
ring-speed speed | Caution Configuring a ring speed that is wrong or incompatible with the connected Token Ring will cause the ring to beacon, which effectively takes the ring down and makes it nonoperational. |
Terminal servers on a Token Ring network in a source-route bridging environment must support the collection and use of RIF information. Use this command to enable collection and use of RIF information:
multiring ipLevel 3 routers that use protocol-specific information rather than MAC information to route datagrams must be able to collect and use RIF information to ensure that the Level 3 routers can transmit datagrams across a source-route bridge. The software default is to not collect and use RIF information for routed protocols. This default allows operation with software that does not understand or properly use RIF information.
When it is enabled, the router will source packets that include information used by source-route bridges. This allows a terminal server with the Token Ring interface to connect to a source-bridged Token Ring network.
RIF information is maintained in a cache whose entries are aged. You can set the number of minutes an inactive RIF entry is kept by using the following command:
rif timeout minutesIf a Token Ring host does not support the use of IEEE 802.2 TEST or XID datagrams as explorer packets, you may need to add static information to the RIF cache of the router/bridge. Use this command to enter static source-route information into the RIF cache:
rif MAC-address [RIF-string] [interface-name]The encapsulation method is changed by using the interface configuration subcommand encapsulation followed by a keyword that defines the encapsulation method.
encapsulation encapsulation-typeFor Ethernet and IEEE 802.3 interfaces, the argument encapsulation-type is arpa. The arpa keyword establishes ARPA Ethernet 2.0 encapsulation, which is the default encapsulation method for Ethernet interfaces.
The snap keyword establishes SNAP encapsulation, which is the IEEE 802.5 MAC-level encapsulation specified by RFC 1042 for Token Ring support and the default encapsulation method for Token Rings.
You do not normally need to change the encapsulation method of an Ethernet or a Token Ring interface.
The serial interfaces support the following kinds of serial encapsulations:
For serial interfaces, the encapsulation-type argument identifies one of the following serial encapsulation types that Cisco Systems' software supports:
The Cisco interface software provides a mechanism for protection against packet overload and resultant recount errors on the MCI interface cards. This mechanism is set using the error-threshold interface subcommand. The syntax is as follows:
error-threshold millisecondsThe argument milliseconds is the frequency at which the error recount will be set. The default is 1000 milliseconds.
The following example sets the error recount threshold on Ethernet interface 0 to 10000 milliseconds.
interface ethernet 0 error-threshold 10000
To disable an interface, use the shutdown subcommand. The command syntax is:
shutdownThis subcommand prevents the transmission of packets on the specified interface.
To restart a disabled interface, use the no shutdown subcommand. The command syntax is:
no shutdownTo check whether an interface is disabled, use the show interface EXEC command. The command syntax is:
show interfaceThis section presents sample network and host configuration files for a terminal server. You can place configuration commands in either or both file types. See the section "Using the Configuration Command" for information about the configure command and the interface and line configuration commands. The last line in a configuration file must be the end keyword.
Duplicating configuration information between the network and the host configuration files does not present a problem. Furthermore, you can place all configuration commands in the host configuration file, reducing the network configuration file to just the end keyword.
However, if conflicting configuration information exists in the network and the host configuration files, the information in the host file takes precedence. This fact allows you to configure all network hosts in general and adjust for specific hosts as necessary.
Comment lines may begin with "!," followed by a space and some text or simply press the Return key (to leave a blank line and improve readability).
The network configuration file contains configuration parameters common to all Cisco Systems terminal servers, routers, and protocol translators on a network. The following list shows a sample network configuration file.
! The "network-confg" file for our network ! ! Define the names and addresses of some special hosts. ip host chaff 192.31.7.18 ip host fuzz 192.31.7.45 ! ! Use a domain server to look up host names. service domain no service ipname name-server 192.31.7.19 domain-name CISCO.COM ! end
The host configuration file contains configuration parameters specific to a terminal server or router host. The following list shows a sample host configuration file that is more complex than most. Generally, a host configuration file contains only a small subset of these commands.
Use the command no exec for unused terminals; setting the speed to a very low number (that is, 110) may prevent loading under certain conditions:
! This is a sample configuration file for chaff. ! ! Define the interface address and subnetting. interface ethernet 0 ip address 192.31.7.18 255.255.255.0 ! ! Define the string to be used in forming the EXEC prompt. hostname chaff ! ! Define a password for the privileged mode. enable-password secret ! ! Define a default gateway only if the network does not have a gateway ! that supports proxy ARP. ip default-gateway 192.31.7.67 ! ! Access list 1 restricts access to hosts on net 192.31.7.0. access-list 1 permit 192.31.7.0 0.0.0.255 access-list 1 deny 0.0.0.0 255.255.255.255 ! ! Set a password on line 0, the console. line 0 location ASM Console password alsosecret ! ! Lines 1 through 7 are in a public terminal area. They are restricted ! to making connections to hosts on the local network. They also run at ! 4800 baud and have padding on the Return character. line 1 7 location Public Terminal Pool access-class 1 out speed 4800 pad 13 25 ! ! Terminal lines 10 through 16 are dial-in modems that ! can run from 300 to 19,200 baud. line 10 16 modem callin autobaud ! ! Lines 17 through 32 are hooked up in reverse connection mode to ! a large terminal switch. By Telnetting to TCP port 3001 on this ! host, a user gets the next free line in the rotary group. line 17 32 rotary 1 modem callout ! ! Line 33 has a laser printer attached. A network printer daemon ! connects to TCP port 4027 on chaff to send data to the printer. ! Software flow control is used and the line speed is set to 38,400 baud. line 33 location Laser Printer/pubs no exec flowcontrol software in flowcontrol software out stopbits 1 txspeed 38400 rxspeed 38400 ! ! Lines 34 through 40 are unused at present. Their line ! speeds are set to zero. line 34 40 location Unused Terminals speed 0 ! ! There are 5 virtual terminals. The vty keyword makes their exact ! line numbers unnecessary. Only hosts specified by ! access list 1 may connect to the virtual terminals. line vty 0 4 access-class 1 in ! ! The end keyword terminates a command file. end
This section lists all of the global system configuration commands in alphabetic order:
Modifies the banner name for the terminal server.
Follow the banner command with one or more blank spaces and any delimiting character (d) you choose. Then type one or more lines of text (message), terminating the message with the second occurrence of the delimiting character.
The banner command has been extended to allow different banners to be displayed depending on exactly how the line is accessed. It is possible to have a distinct message displayed on incoming connections and outgoing connections. In addition, a second banner is available to display messages of a changeable nature on both types of connections.
To be able to display a message when an EXEC process is created, use the banner exec global configuration command.
This specifies a message to be displayed when an EXEC process is created (line activated, or incoming connection to VTY).
To display incoming message on a particular terminal line, use the banner incoming global configuration command.
This specifies a message to be displayed on incoming connections to particular terminal lines, for example, lines used for "milking machine" applications.
To specify a general-purpose message-of-the-day type banner, use the banner motd global configuration command.
This is displayed message-of-the-day type banner whenever a line is activated or when an incoming Telnet connection is created.
Specifies the size of the buffer to be used for netbooting a host or a network configuration file.
The argument bytes specifies the size of the buffer to be used. By default, it is the size of non-volatile memory, and there is no minimum or maximum size that may be specified.
[no] boot host filename [address]
Changes the host configuration file name.
The keyword host changes the host configuration file name to a name you specify in the filename argument.
[no] boot network filename [address]
Specifies the name of this file; use the network configuration file.
The keyword network changes the network configuration file.
The argument filename is the new name for the network configuration file.
The argument address is the new broadcast address. If you omit the argument address, the terminal server uses the default broadcast address of "255.255.255.255." If you use address, you can specify a specific network host or a subnet broadcast address.
[no] boot system filename [address]
Specifies the name of an operating system image file to load across the network.
The keyword system indicates that the file name and host addresses for booting operating software over the network are in the non-volatile memory.
The argument filename is the file name of the operating software to load, and the argument address is the address of the network host holding that file.
[no] buffers {small|middle|big|large|huge} {permanent|max-free|min-free|initial} number
Allows a network administrator to adjust initial buffer pool settings and set limits at which temporary buffers are created and destroyed.The first argument denotes the size of buffers in the pool; the default number of the buffers in a pool is determined by the hardware configuration. The second argument specifies the buffer management parameter to be changed, as follows:
The no buffers command with appropriate keywords and arguments restores the default buffer values.
[no] busy-message hostname d message d
Sets a message that the terminal server displays whenever an attempt to connect to the specified host fails.
The argument hostname is the name of the host. Follow the argument hostname with one or more blank spaces and any delimiting character (d) you choose. Then type one or more lines of text (message), terminating the message with the second occurrence of the delimiting character.
Assigns a password for the privileged command level.
The argument password is case-sensitive and specifies the password prompted for in response to the EXEC command enable.
[no] enable last-resort {succeed|password}
Allows the user to specify what happens if the TACACS server used by the enable command does not respond. The default is to fail.
The keyword succeed allows the user to enable without further question.
The keyword password allows the user to enable by entering the privileged command level.
The no enable last-resort command restores the default.
Use TACACS to check the user ID and password supplied to the EXEC enable command.
Defines extra baud rates for the system, in place of 38400.
The argument number defines the extra baud rates available for the system. Possible baud rate values are: 57600, 38400, 28800, 23040, 16457, 14400, 12800, and 11520.
Modifies the host name for the terminal server.
The argument name is the new host name for the network server and is case-sensitive. The default host name is "gateway."
Allows a terminal to be temporarily "locked" by the EXEC command lock.
The no lockable command reinstates the default, which does not allow the terminal to be locked.
Identifies a syslog server host to receive logging messages.
The argument host is the name or the Internet address of the host.
By issuing this command more than once, you build a list of syslog servers that receive logging messages.
The no logging command deletes the syslog server with the specified address from the list of syslogs.
Copies logging messages to an internal buffer instead of writing them to the console terminal.
The buffer is circular in nature, so newer messages overwrite older messages.
The no logging buffered command cancels the use of the buffer and writes messages to the console terminal, which is the default.
Limits the logging messages displayed on the console terminal to messages with a level at or below level.
The argument level is one of the following keywords, listed here in order from the most severe to the least severe level.
The default is to log messages to the console at the warnings level.
The no logging console command disables logging to the console terminal.
Limits the logging messages displayed on terminal lines other than the console line to messages with a level at or above level.
The argument level is one of the keywords described for the logging console command in the section "Logging Messages to the Console."
The no logging monitor command disables logging to terminal lines other than the console line.
Enables message logging to all destinations except the console. This behavior is the default.
The no logging on command enables logging to the console terminal only.
Limits the logging messages sent to syslog servers to messages with a level at or above level.
The argument level is one of the keywords described for the logging console command in the section "Logging Messages to the Console."
The no logging trap command disables logging to syslog servers.
[no] login-string hostname d message [%secp] [%secw] [%b]d
[no] login-string hostname
Defines a string of characters that the terminal server sends to a host after a successful connection attempt. The argument hostname is the name of the host to receive the message. Follow hostname with one or more blank spaces and a delimiting character d you choose. Then, type one or more lines of text message, terminating the message with the second occurrence of the delimiting character. This command applies only to rlogin and Telnet sessions.
The %secp option sets a pause in seconds.
The %secw option prevents users from issuing commands or keystrokes during a pause.
The %b option sends a Break character.
Disables the SNMP server after it has been started.
Tailors use by the network server of network-based services.
The no service subcommand disables the specified service or function.
The argument keyword is one of the following:
[no] service tcp-keepalives-in
[no] service tcp-keepalives-out
The command service tcp-keepalives-in enables keepalives on incoming connections (connections initiated by a remote host). The command service tcp-keepalives-out enables keepalives on outgoing connections (connections initiated by a user of the terminal server).
The no service tcp-keepalives-in and no service tcp-keepalives-out commands disable support of the keepalives protocol. This is the default.
[no] snmp-server access-list list
Sets up an access list that determines which hosts can send requests to the terminal server.
The argument list is an integer from 1 through 99 that specifies an access list. The access list applies only to the global read-only SNMP agent configured with the command snmp-server community.
The snmp-server access-list is a global command that sends all traps to the host. The terminal server ignores packets from hosts that the access list denies.
The no snmp-server access-list command removes the specified access list.
[no] snmp-server trap-authentication
Enables the network server to send a TRAP message when it receives a packet with an incorrect community string.
The SNMP specification requires that a TRAP message be generated for each packet with an incorrect community string. However, because this action can result in a security breach, the network server by default does not return a TRAP message when it receives an incorrect community string.
[no] snmp-server community [string [RO|RW] [list]]
Sets up the community access string. This command enables SNMP server operation on the terminal server. The argument string specifies a community string that acts like a password and permits access to the SNMP protocol.
By default, an SNMP community string permits read-only access (keyword RO); use the keyword RW to allow read-write access. The optional argument list is an integer from 1 through 99 that specifies an access list of Internet addresses that may use the community string.
The no snmp-server community command removes the specified community string or access list.
[no] snmp-server host address community-string cb [snmp|tty]
Specifies which host or hosts should receive TRAP messages. You need to issue the snmp-server host command once for each host acting as a TRAP recipient.
The argument address is the name or Internet address of the host. The argument community-string is the password-like community string set with the snmp-server community command.
The optional keyword snmp causes all SNMP-type TRAP messages to be sent and sends the Cisco-specific RELOAD TRAP message.
The optional keyword tty causes TCP connection TRAP messages to be included.
The no snmp-server host command removes the specified host.
Allows control over the largest SNMP packet size permitted when the SNMP server is receiving a request or generating a reply.
The argument bytes is a byte count from 484 through 8192. The default is 484.
snmp-server queue-length length
Establishes the message queue length for each TRAP host. It defines the length of the message queue for each TRAP host.
The argument length is the number of TRAP events that can be held before the queue must be emptied; the default is 10. Once a TRAP message is successfully transmitted, software will continue to empty the queue, but never faster than at a rate of four TRAP messages per second.
[no] snmp-server system-shutdown
Requesting "shutdown-after-message" is similar to issuing a send command followed by a reload command. Because the ability to cause a reload from the network is a powerful feature, it is protected by this configuration command. To use this SNMP message reload feature the device configuration must include the snmp-server system-shutdown global configuration command.
The no snmp-server system-shutdown option prevents an SNMP system-shutdown request (from an SNMP manager) from resetting the Cisco agent.
[no] snmp-server trap-authentication
Enables the network server to send a TRAP message when it receives a packet with an incorrect community string.
The SNMP specification requires that a TRAP message be generated for each packet with an incorrect community string. However, because this action can result in a security breach, the network server by default does not return a TRAP message when it receives an incorrect community string.
snmp-server trap-timeout seconds
Defines how often to try resending TRAP messages on the retransmission queue. The argument seconds sets the interval for resending the messages.
The default is set to 30 seconds.
state-machine name state firstchar lastchar nextstate|transmit [delay]
Specifies the transition criteria for the state of a particular state machine.
The argument name is the user-specified name for the state machine (specified by the dispatch-machine line subcommand). There can be any number of state machines specified by the user, but each line can only have a single state machine associated with it.
The argument state defines which state is being modified. There are a maximum of eight states per state machine. Lines are initialized to state 0, and return to state 0 after a packet is transmitted.
The arguments firstchar and lastchar specify a range of characters. If the state machine is in the indicated state, and the next character input is within this range, go to the specified next state. Full 8-bit character comparisons are done, so the maximum value is 255. Make sure that the line is configured to strip parity bits (or not generate them) or duplicate the low characters in the upper half of the space.
The argument nextstate defines the state to enter if the character is in the specified range.
Specifying the transmit keyword causes the packet to be transmitted, and the state machine to be reset to state 0. Characters that have not been explicitly defined to have a particular action return the state machine to state 0.
The optional delay keyword specifies that the destination state is transitory. If no additional input is received, the packet will be sent after 100 ms, and the state reset to 0.
[no] tacacs-server attempts count
Controls the number of login attempts that may be made on a line set up for TACACS verification. The argument count is the number of attempts. The default is three attempts.
The no tacacs-server attempt subcommand restores the default.
tacacs-server authenticate {connect|slip|enable}
Causes the terminal server to require a response from the TACACS server to indicate whether the user may perform the indicated action. Actions which require a response include the following, specified as optional keywords:
Enables an extended TACACS mode. This mode provides information about the terminal requests for use in setting up UNIX auditing trails and accounting files for tracking use of devices which use extended TACACS. This information includes responses from devices and validation of user requests. An unsupported, extended TACACS server is available from Cisco Systems for UNIX users who want to create the auditing programs.
[no] tacacs-server last-resort {password|succeed}
Causes the network server to request the privileged password as verification, or forces successful login without further input from the user, depending upon the keyword specified.
The keyword password allows the user to access the privileged level command mode by entering the password set by the enable command.
The keyword succeed allows the user to access the privileged level command mode without further question.
The no tacacs-server last-resort command restores the system to the default behavior.
Specifies a TACACS host. The argument name is the name or Internet address of the host. You can use multiple tacacs-server host subcommands to specify multiple hosts. The server will search for the hosts in the order you specify them.
The no tacacs-server host subcommand deletes the specified name or address.
tacacs-server notify {connect|slip|enable|logout}
Causes a message to be transmitted to the TACACS server, when various event occur.
The optional keywords are used to specify notification of the TACACS server whenever someone does one of the following things:
[no] tacacs-server retransmit retries
Specifies the number of times the server will search the list of TACACS server hosts before giving up. The server will try all servers, allowing each one to time-out before increasing the retransmit count. The argument retries is the retransmit count. The default is two retries.
The no tacacs-server retransmit subcommand restores the default.
[no] tacacs-server timeout seconds
Sets the time interval that the server waits for a server host to reply. The argument seconds specifies the number of seconds. The default interval is 5 seconds.
The no tacacs-server timeout subcommand restores the default.
username name [nopassword | password encryptiontype password]
username name [accesslist number]
username name [autocommand command]
username name [nopassword], [noescape], [nohangup]
Specifies options for a single user.
The nopassword keyword means that no password is required for this user to log in. This is usually most useful in combination with the autocommand keyword.
The password keyword specifies a possibly encrypted password for this user name.
The encryptiontype argument is a single digit number. Currently defined encryption types are 0, which means no encryption, and 7, which specifies a Cisco-specified encryption algorithm. Passwords entered unencrypted are written out with the Cisco encryption. Passwords can contain imbedded spaces and must be the last option specified in the username command.
The accesslist keyword specifies an outgoing access list to be used for the life of the user's login. The access list number is specified by the number argument.
The autocommand keyword causes the command specified by the command argument to be issued automatically after the user logs in. When the command is complete, the session is terminated. As the command can be any length and contain imbedded spaces and such, commands using the autocommand keyword must be the last option on the line.
The nohangup keyword prevents the terminal server from disconnecting the user's conection after an automatic command (set up with the autocommand keyword) has completed. Another login prompt is provided to the user.
This section lists all of the line configuration subcommands in alphabetic order:
[no] activation-character decimal-number
Sets the activation character. The activation-character subcommand defines the character you type at a vacant terminal to begin a terminal session.
The argument decimal-number is the ASCII decimal representation of the activation character. The default activation character is Return (ASCII character 13).
The no activation-character subcommand causes any character to activate a terminal.
Sets the line to autobaud. The autobaud subcommand specifies automatic baud-rate detection over a range from 300 to 19200 baud. The no autobaud subcommand disables the autobaud feature.
Causes the EXEC to issue the exit command when the last connection closes.
Causes a line to automatically establish a connection to a host when an EXEC is started.
The argument connect-argument is any text appropriate as an argument to the connect EXEC command, including the host name and any switches.
The autohost command is typically used to force an automatic call to a particular host when a user connects to a designated line on the terminal server.
Sets the number of data bits per character. If parity is being generated, specify 7 data bits per character. If no parity generation is in effect, specify 8 data bits per character.
The default is 8 data bits per character.
[no] disconnect-character decimal-number
Defines the character you type to end a session with the terminal server.
The argument decimal-number is the ASCII decimal representation of the session-disconnect character.
[no] dispatch-character decimal-number1 [decimal-number2 . . . decimal-number]
Defines a character that causes the packet to be sent, even if the dispatch timer has not expired.
The argument decimal-number is the ASCII decimal representation of the character, such as Return (ASCII character 13) for line-at-a-time transmissions.
The no dispatch-character subcommand removes the definition of the specified dispatch character.
Specifies the name of the state machine to determine when to send packets on the asynchronous line.
[no] dispatch-timeout milliseconds
Sets the dispatch timer.
The argument milliseconds specifies the number of milliseconds the terminal server waits after putting the first character into a packet buffer before sending the packet. During this interval, more characters may be added to the packet, thus increasing the processing efficiency of the remote host.
The no dispatch-timeout subcommand removes the time-out definition.
[no] escape-character decimal-number
Defines the escape character and reinstates the default escape.
The argument decimal-number is either the ASCII decimal representation of the character or a control sequence (Ctrl-E, for example).
The default escape character is Ctrl-^.
The no escape-character subcommand reinstates the default escape character.
This EXEC subcommand determines whether or not the terminal server will start an EXEC process on the line. A serial printer, for example, should not have an EXEC started.
By default, the terminal server starts EXECs on all lines.
[no] exec-timeout minutes [seconds]
Sets a time interval before returning the terminal to the idle state.
The argument minutes is the number of minutes.
The optional argument seconds specifies additional interval time in seconds. The default interval is 10 minutes; an interval of 0 (zero) specifies no time-outs.
The no exec-timeout subcommand removes the time-out definition. It is the same as entering exec timeout 0.
flowcontrol {none | software [in | out] | hardware}
Sets the method of data flow control between the terminal or other serial device and the terminal server.
The keyword software sets software flow control.
An additional keyword specifies the direction: in causes the terminal server to listen to flow control from the attached device, and out causes the terminal server to send flow control information to the attached device. If you do not specify a direction, both are assumed.
For software flow control, the default stop and start characters are Ctrl-S and Ctrl-Q (XOFF and XON). You can change them with the stop-character and start-character subcommands.
The keyword hardware sets hardware flow control. For information about hardware flow control, see the relevant Cisco Hardware Installation and Reference publication. Only limited modem control is possible on a line using hardware flow control.
No modem control is necessary on a line utilizing hardware flow control.
By default, no flow control method is set for a line.
[no] hold-character decimal-number
Defines the local hold character used to pause output to the terminal screen. The argument decimal-number is either the ASCII decimal representation of the hold character or else a control sequence (for example, Ctrl-C). The Break character is represented by 0 (zero); NUL cannot be represented.
By default, no local hold character is defined.
Sets the line as in an insecure location. This line subcommand applies only to LAT connections.
Sets the terminal screen length.
The argument screen-length is the number of lines on the screen.
line [type-keyword ]first-line [last-line]
Takes up to three arguments: a keyword, a line number, or a range of line numbers.
The optional argument type-keyword specifies the type of line to be configured; it is one of the following keywords:
When the line type is specified, the argument first-line is the relative number of the terminal line (or the first line in a contiguous group) you want to configure. Numbering begins with 0 (zero).
The optional argument last-line then is the relative number of the last line in a contiguous group you want to configure.
If you omit type, then first-line and last-line are absolute rather than relative line numbers. To display absolute line numbers, use the EXEC command systat.
Enables use of an auxiliary RS-232 DTE port available on all processor cards. The port-address argument is 1 on Cisco terminal servers. This port is not available on the STS-10x.
Enters information about the terminal location and/or status.
The argument text is the desired description. The description appears in the output of the EXEC command systat.
Causes the terminal server to prompt for a password before starting the EXEC process when you have set a password for the line.
The no login line subcommand disables the password checking behavior described above and allow connections without a password.
Sets up the TACACS verification mechanism to handle the password checking.
The no login tacacs subcommand disables TACACS password checking.
Configures a modem control line. The argument keyword is one of the modem control keywords described in this chapter under "Configuring the Modem Control Lines."
The no modem subcommand removes modem control from a line.
By default, a terminal line is configured for no modem control.
Sets the interval during which the terminal server raises DTR in response to RING and the modem responds to CTS. This behavior is useful for modems that take a long time to synchronize to the appropriate line speed.
The argument seconds specifies the interval in seconds.
The default is 15 seconds.
Configures support for dial-in modems that use DTR to control the off-hook status of the telephone line. Raising the DTR signal answers the telephone; lowering DTR hangs up the telephone.
Configures support of ports connected to computers that expect to be connected to modems, an arrangement often called "milking machine" mode. (For more information, refer to the section on "Configuring Reverse Connections" in this chapter). This subcommand causes the terminal server to behave somewhat like a modem.
Configures modem control lines to support lines that either the user or the network can activate.
Configures a line to leave DTR low unless the line has an active TCP connection in either direction.
Enables a line to be used for both incoming and outgoing calls on dial-in/dial-out modems. Note that the terminal server does not support any dialing protocols. Therefore, the host system software or the user must provide any special dialing commands when using the modem for outgoing calls.
Configures support for modems that can handle telephone line protocols, such as answering the telephone after a certain number of rings.
Sets a line to inform a user who has multiple, concurrent Telnet connections when output is pending on a connection other than the current connection.
This subcommand performs the same function as the EXEC command terminal notify described in the chapter "Managing the System."
The no notify subcommand ends notification.
[no] padding decimal-number count
Sets padding for a specified output character.
The argument decimal-number is the ASCII decimal representation of the character.
The argument count is the number of NUL bytes sent after that character.
The no padding subcommand removes padding for the specified output character.
parity {none | even | odd | space | mark}
Defines the generation of the parity bit. By default, the terminal server does no parity checking.
Specifies a password.
The text argument may contain any alphanumeric characters, including spaces, up to 80 characters. The password checking is also case-sensitive.
The password Secret is different than the password secret, for example, and the password two words is an acceptable password.
The no password line subcommand removes the password.
Ensures that the configuration options the user can set remain in effect between terminal sessions.
This behavior is desirable for terminals in private offices.
By default, user-set configuration options are cleared with the EXEC command exit or when the interval set with the exec-timeout subcommand has passed.
[no] refuse-message d message d
Allows you to define the error message generated when a user attempts to connect to a line that is busy.
The argument d is a delimiting character of your choice.
The argument message is the message you want to show on the terminal.
Define each group of lines.
The rotary subcommand adds a line to the specified rotary group.
The argument group is an integer you choose between 1 and 100 that identifies the rotary group.
[no] session-limit session-number
Sets the maximum number of concurrent sessions allowed. The argument session-number specifies the maximum number of sessions.
[no] session-timeout minutes [output]
Sets the interval the terminal server waits for traffic before closing the connection to a remote computer and returning the terminal to the idle state.
The argument minutes specifies the interval in minutes.
The optional keyword output specifies that when traffic is sent to an asynchronous line from the terminal server (within the specified interval), the connection is retained. If not specified, the session time-out interval is based only user input, not output.
The default interval is 0 (zero), indicating the terminal server maintains the connection indefinitely.
speed baud
txspeed baud
rxspeed baud
The speed subcommand sets both the transmit (to terminal) and receive (from terminal) speeds.
The txspeed subcommand sets the transmit speed only.
The rxspeed subcommand sets the receive speed only.
The argument baud can be 300, 1200, 2400, 4800, 9600, 19200, or 38400.
The default speed is 9600 baud.
The stopbits subcommand sets the number of stop bits transmitted per byte. By default, the terminal server sends 2 stop bits.
The stop-character subcommand defines the character that signals the end of data transmission when software flow control is in effect.
The argument decimal-number is the ASCII decimal representation of the stop character.
The default stop character is Ctrl-S (ASCII character 19).
start-character decimal-number
Defines the character that signals the start of data transmission when software flow control is in effect.
The argument decimal-number is the ASCII decimal representation of the start character.
The default start character is Ctrl-Q (ASCII character 17).
[no] terminal-type terminal-name
The terminal-type subcommand records, in the argument terminal-name, the type of terminal connected to the line for use in Telnet terminal-type negotiation; the Telnet terminal-type negotiation uses terminal-name to inform the remote host of the terminal type. Terminal type is used by by TN3270 for display management.
The no terminal-type subcommand removes the information about the type of the terminal.
transport input [telnet] [lat] [none]
Specifies which protocols may be used for input on a line.
transport output [telnet] [lat] [rlogin] [none]
Specifies which protocols may be used for output on a line.
transport preferred [telnet|lat|rlogin|none]
Specifies the preferred protocol to use when a command does not specify one.
[no] vacant-message
vacant-message d message d
The vacant-message subcommand enables the banner to be displayed on the screen of an idle terminal.
The vacant-message subcommand without any arguments causes the default message to be displayed.
If a banner is desired, follow the vacant-message subcommand with one or more blank spaces and a delimiting character (d) you choose. Then type one or more lines of text (message), terminating the text with the second occurrence of the delimiting character.
Sets the number of characters columns on a single line of the attached terminal.
This section list all of the configuration subcommands in alphabetic order:
encapsulation encapsulation type
Specifies an encapsulation method for the interface.
For Ethernet and IEEE 802.3 interfaces, the argument encapsulation-type is arpa. The arpa keyword establishes ARPA Ethernet 2.0 encapsulation, which is the default encapsulation method for Ethernet interfaces.
For serial interfaces, the encapsulation-type argument identifies one of the following serial encapsulation types that Cisco Systems' software supports:
Specifies the frequency with which the error count will be reset, use the error-threshold interface subcommand.
The argument milliseconds is a time measurement in milliseconds. The default is 1000.
Identifies a specific interface for configuration and starts interface configuration command collection.
The argument type is ethernet for an Ethernet interface, tokenring for a Token Ring interface, and serial for a supported serial interface.
The argument unit is a positive integer that specifies the nth interface of type type, starting with 0 for the first interface of that type. The terminal server can have only one network interface of each type, so unit is always 0.
Prevents the transmission of packets on the specified interface by disabling the interface.
Use the no shutdown command to restart a disabled interface.
This section lists the system configuration EXEC commands in alphabetic order.
Begins configuration.
Disables privileged command level.
Enables the privileged command level.
|
|